What is ClickFix phishing?
In this post, we will explore what ClickFix phishing is and how you can simulate it in a phishing campaign. We will be using Phishing Club, but this methodology could be applied to almost any phishing simulation software.
ClickFix is a phishing tactic where malicious attackers attempt to get recipients to execute a nefarious command. The execution of this command could steal sensitive information, install malware, info stealers, or other malicious tools.
A great example is the 'FakeCaptcha' variant of ClickFix phishing, where the recipient unknowingly ends up on a phishing page that shows a 'not a robot' test, asking them to prove they are not a robot by entering a few shortcuts on their keyboard.
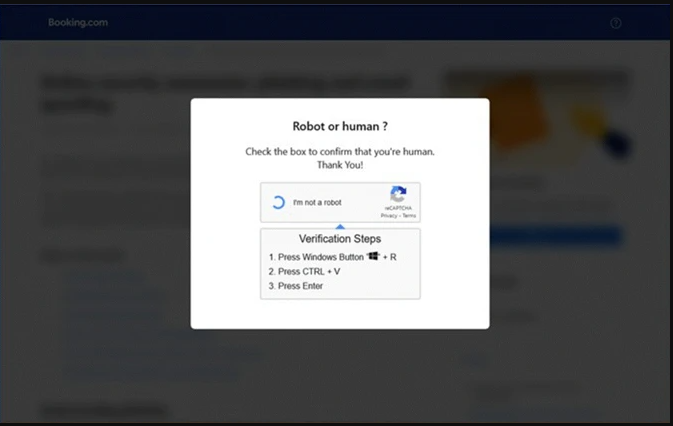
In the booking.com ClickFix phishing campaign, the attack works by:
- A malicious script is copied into the clipboard automatically when visiting the page or interacting with the content.
CTRL + WIN
This shortcut opens 'cmd.exe'.CTRL + V
Pastes the command.ENTER
Executes the command.
This payload targets Windows operating systems, but it could be adapted for Linux and Mac. There are also variants that try to trick recipients into pasting malicious commands through other vectors, such as the browser console.
Now that we understand how ClickFix attacks work, let's explore how to simulate them safely for security awareness training.
Prerequisites and Warnings
⚠️ Important Considerations ⚠️
When simulating phishing in a Microsoft tenant, allowlisting via advanced delivery should be set up prior to the tests. This ensures that the lures are received by recipients and the tests are targeting humans and not defensive products. Another important aspect is that Microsoft handles reported phishing incidents differently when the sender and simulation URLs have been allowlisted.
However, when executing ClickFix, the attack vector executes code on the recipient's machine, which is outside of what is allowlisted. This might very well trigger Defender and/or EDR warnings. Make sure that the IT provider or SOC knows what to expect to quickly remediate any false positives triggered by the test.
Simulating ClickFix phishing
It is very easy to simulate a ClickFix campaign. All you need to do is change the command the recipient copies and pastes into something that makes a POST request back to the phishing simulator, similar to a user submitting a form.
To show how this can be done, I will put together a small example campaign.
In this example, we will use Phishing Club's multi-page feature to create the flow of phishing pages. However, the setup can also be done using a single page with a bit more coding.
The simulation consists of:
- Email mimicking Microsoft with an urgent warning
- A pre-landing page that checks that the user is not using a mobile device
- A landing page with a Captcha variant of ClickFix
- An offboarding page
Let's walk through each component of this simulation to understand how they work together to create an effective training scenario.
The Phishing Email
For the purpose of ClickFix simulation, any lure that activates the recipient can be effective. In this example, we will use a simple warning email from Microsoft urging the recipient to take action before their account is disabled.
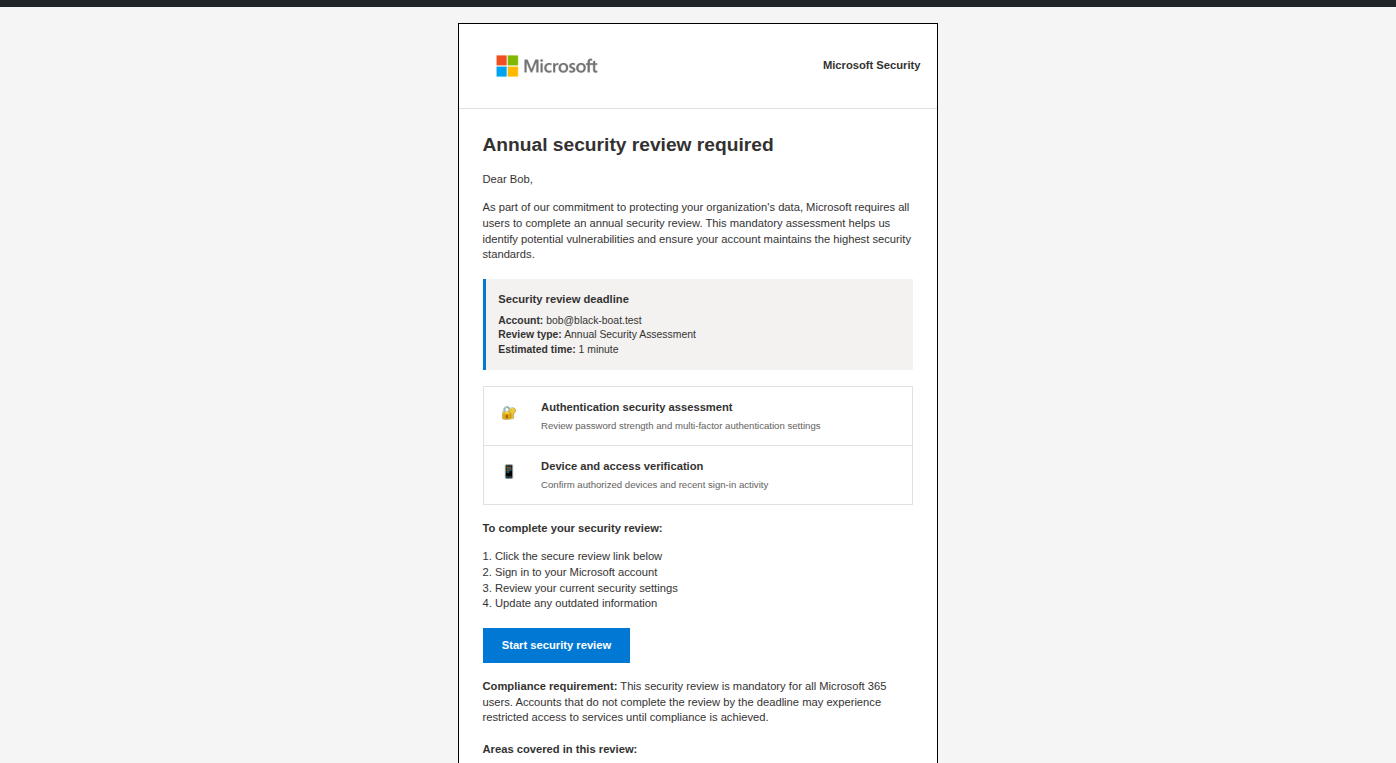
Once the recipient clicks the link in the email, they need to be directed through a series of pages designed to make the ClickFix attack believable and effective.
Mobile Gate Page (Optional)
This step is completely optional but can help increase the success rate of your simulation. When a recipient clicks on the phishing lure, we want to increase the chances that they can execute the payload. In this example, we are using a Windows variant, so if the user is detected using a mobile device, we will show a page stating they must be on a PC to complete the process.
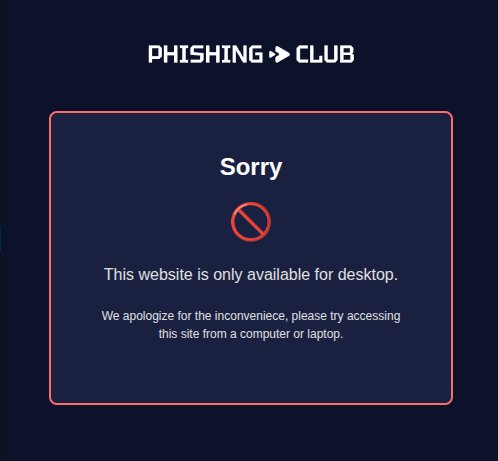
We could also add checks that investigate the operating system and tailor different steps and payloads depending on whether it's Windows, Linux, or Mac. For this demonstration, we'll focus on the Windows variant.
After ensuring the user is on the right platform, we can now present them with the main ClickFix simulation.
The ClickFix Landing Page
For the landing page, we will be using John Hammond's recaptcha phish example with a bit of modification: we will replace a broken image and place it in the middle of an example page.
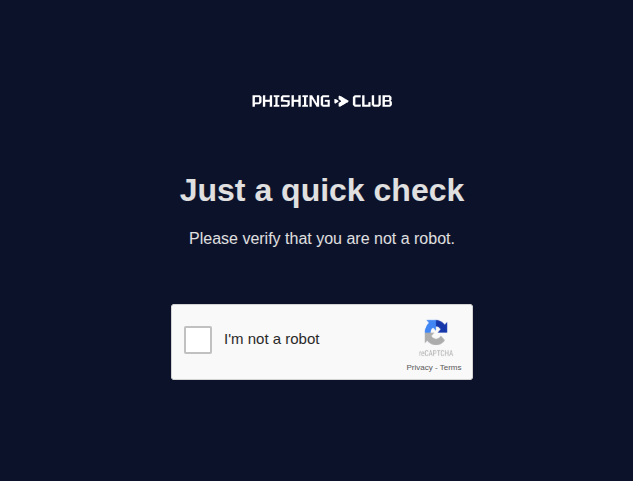
When the recipient interacts with the ReCaptcha, it will show the malicious instructions:
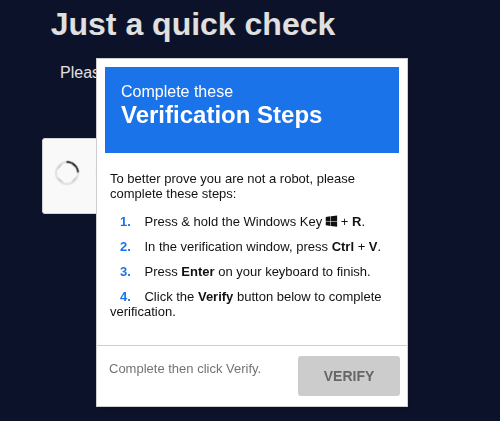
Changing the payload
To ensure we get the metrics in the phishing platform from a completed interaction, we must ensure that the script executed sends back a POST request to the phishing server. This should do the trick in Phishing Club, GoPhish, and most commercial SaaS platforms.
So simulating a ClickFix attack is actually really simple. All you have to do is ensure that the script the user is tricked into running sends a POST request to the phishing server, as if it was a form submission.
The payload used in this example will send a POST request back to the phishing server to the same URL as if it was a form submission.
curl -s -X POST {{.URL}}Once the user executes this command, they've fallen for the simulation. Now it's time to educate them about what just happened.
Educational Offboarding
Finally, after the recipient has fallen prey to the phishing simulation, we show them an offboarding page.
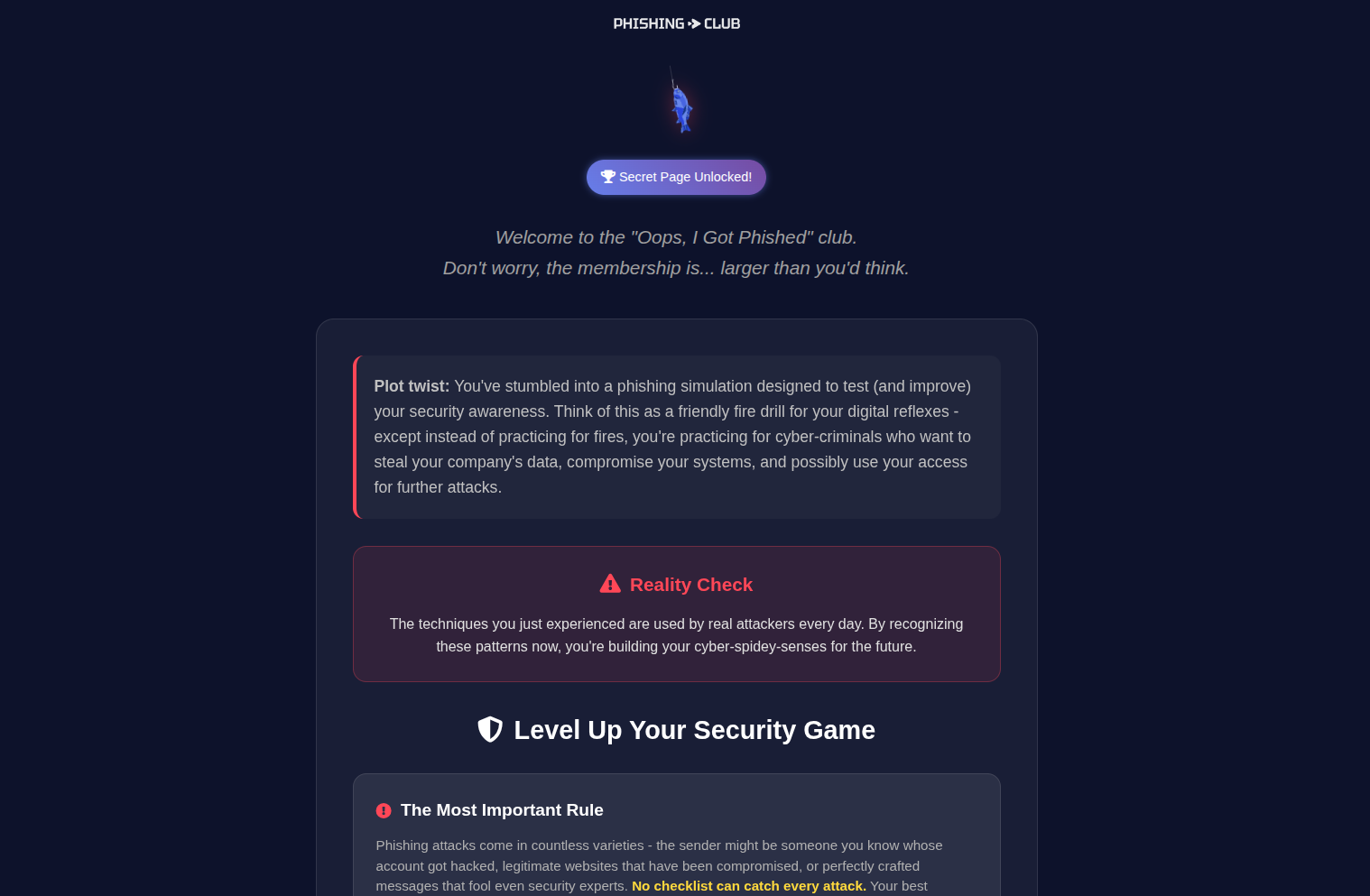
Depending on what kind of phishing simulation program you are running, this might be one of the following:
- "You've been phished" page - With supportive and quickly digestible information about the simulation.
- "Nothing to see here" page - Has the purpose of diverting the recipient's attention so they do not notice they've been phished.
With all the individual components designed, the next step is to chain them together into a cohesive campaign using your phishing simulation platform.
Implementation: Setting up the Campaign in Phishing Club
To implement this ClickFix simulation in Phishing Club, you'll need to set up a template that chains multiple pages together. The platform's template system makes this process straightforward by allowing you to create a multi-step campaign flow.
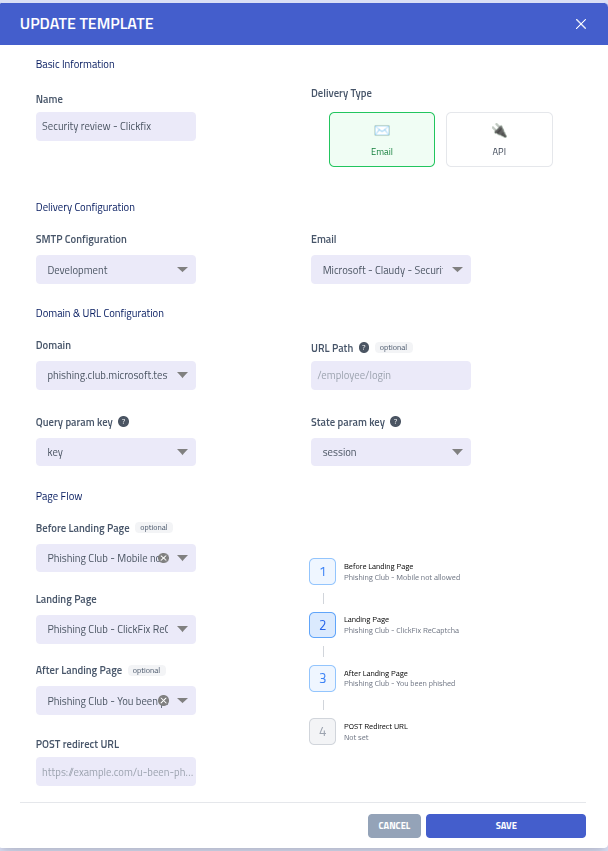
The template configuration shown above demonstrates how to structure your ClickFix campaign:
- Email Template: The initial lure that drives recipients to the landing page
- Mobile Gate Page: Device detection and OS verification (optional)
- Main Landing Page: The ClickFix/Captcha simulation
- After Landing Page: Quick and short educational content
By using Phishing Club's chaining feature, you can create a seamless flow that guides recipients through each stage of the simulation while collecting valuable metrics at each step. This approach allows you to track where users drop off and measure the effectiveness of different components in your ClickFix simulation.
Staying Ahead of ClickFix Threats
ClickFix phishing represents a significant threat in social engineering tactics. By understanding how these attacks work and implementing realistic simulations, organizations can better prepare their users to recognize and respond to these sophisticated threats.
The key to effective ClickFix training is creating realistic scenarios that help users develop a healthy skepticism of unexpected error messages and technical instructions, while providing clear guidance on proper verification procedures.
As cybercriminals continue to refine their ClickFix techniques, organizations must stay vigilant and adapt their security awareness programs accordingly. With tools like Phishing Club, implementing comprehensive ClickFix simulations becomes straightforward and effective, enabling organizations to stay one step ahead of emerging threats.


