Recipients
Recipients are the target users for your phishing. Recipient must be placed in groups to be targets of a campaign.
Overview
The recipients page displays recpients along with their information and analytics. Recipients
flagged as
Repeat Offenders are marked.
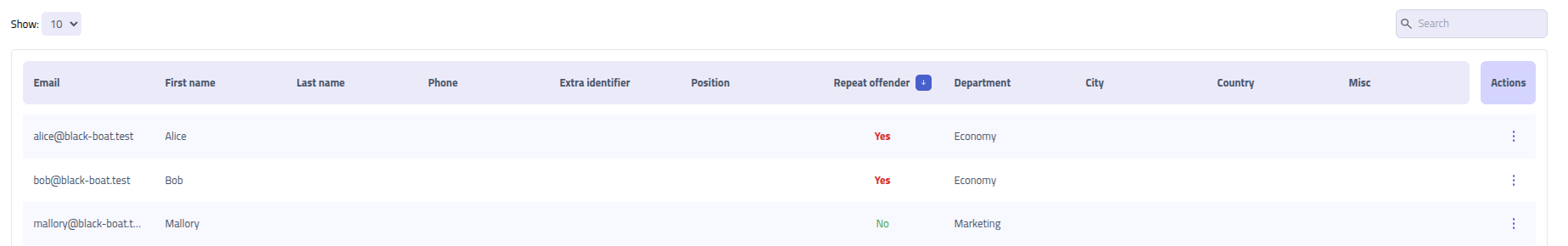
Click on a recipient name to see more details about them.
Create new recipient
Recipients can manually be typed via. the create recipient modal.
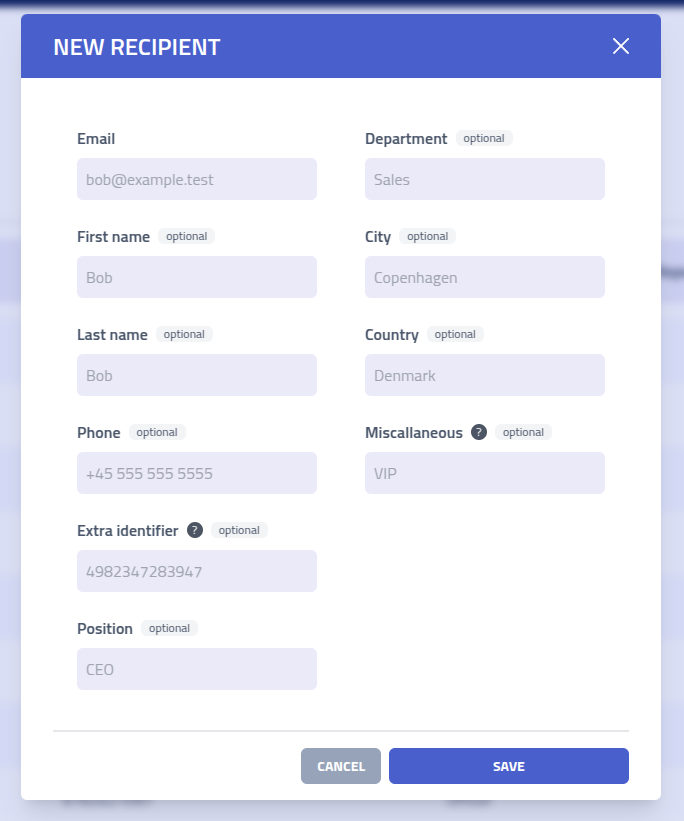
Each field serves can be used as a variable variable in emails and pages.
| Field | Description |
|---|---|
| Email Address | Unique email address |
| First Name | |
| Last Name | |
| Phone Number | |
| Extra Identifier | Additional unique identifier such as employee ID, username, or etc. |
| Position | |
| Department | |
| City | |
| Country | |
| Miscallaneous | Custom field |
Privacy Recommendation: Follow data minimization principles by adding only the information necessary for your specific campaign objectives. For most phishing, only the email is needed.
Import from CSV
Use the CSV import functionality to import multiple recipients at once.
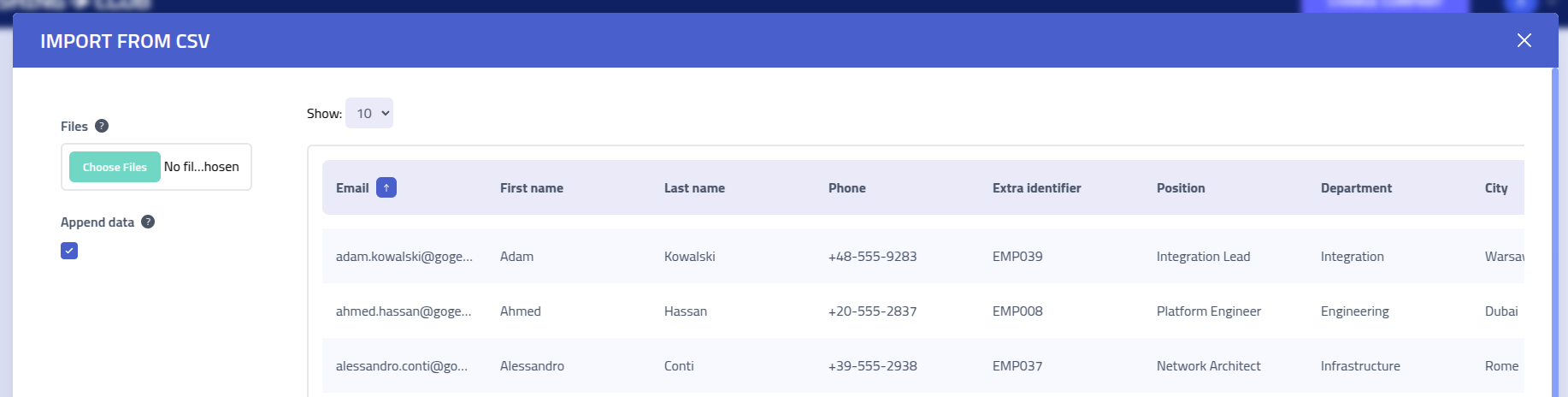
CSV File Format
Your CSV file must include a header row with column names matching the recipient profile fields. The system maps columns to recipient attributes based on these headers.
Here's an example of a properly formatted CSV file:
Email,Phone,ExtraIdentifier,FirstName,LastName,Position,Department,City,Country,Misc "[email protected]","+1-555-0191","EMP001","Marcus","Jenkins","Solutions Architect","Engineering","Portland","USA","Kubernetes Expert" "[email protected]","+7-916-555-0847","EMP002","Elena","Popov","Data Scientist","Analytics","Moscow","Russia","ML Specialist" "[email protected]","+91-555-8273","EMP003","Raj","Patel","DevOps Engineer","Operations","Mumbai","India","Docker Certified" "[email protected]","+47-555-9182","EMP004","Hannah","Berg","Product Owner","Product","Oslo","Norway","Agile Coach"
Recipient details
Each recipient has a page that provides analytics, which groups the recipient has been added to, and an overview of which events they created.
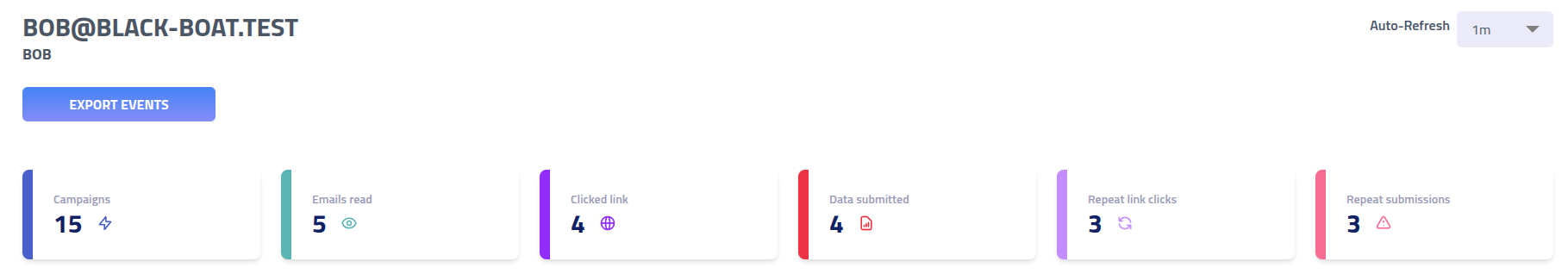
The score cards in the top display the recipients analytics across all campaigns:
| Field | Description |
|---|---|
| Total Campaigns | Number of phishing simulations this recipient has participated in |
| Emails Opened | Unique email opens tracked via embedded tracking pixels |
| Initial Link Clicks | First-time clicks on phishing links per campaign |
| Data Submissions | Number of campaigns where recipient submitted personal information through phishing forms |
| Reported | Number of campaigns the recipient has reported |
| Repeat Offenses (Links) | Pattern of clicking phishing links across multiple campaigns |
| Repeat Offenses (Data) | Pattern of submitting sensitive information across multiple campaigns |
Export
Use the Export Events button to download a export for the recipients data.
The export includes recipient.csv with the recipients personal data and a
events.csv includes all events associated with the recipient.

