Software Management
System Requirements
Phishing Club is designed to work with most Linux distributions and provides installation and update functionality for systems using systemd.
Deploy on infrastructure where hardware resources can be scaled to accommodate your usage patterns and campaign requirements.
A simple instance can run on a very low requirement of cpu and ram (1 cpu, 1 gb ram, probably a lot less), while long term use of Phishing Club might require a beefy setup.
Quick Install
For AMD64 systemd-enabled distributions, run the following command on your server:
curl -fsSL https://raw.githubusercontent.com/phishingclub/phishingclub/main/install.sh | bash
This will start an interactive installer. Remember to copy the password after installation.
Manual install
Download the latest AMD64/ARM64 version of Phishing Club from Github.
Images
Find the latest AMD64/ARM64 images for download on Github (ghrc.io).

Running the binary with the --install flag launches an installer that handles the
setup process. The installer handles configuration, dependency installation, creates a
phishingclub user and group, sets up a systemd service, and copies the binary to
/opt/phishingclub.
This approach ensures the application runs with an unprivileged user account and starts on system reboots.
For manual setup, use the --help command to view all available options and configuration
parameters.
Step-by-Step Installation
Transfer the Binary
Transfer the downloaded binary to your target server:
scp ./phishingclub [email protected]:/tmp/
Prepare for Installation
Connect to your server and make the binary executable:
ssh [email protected] cd /tmp chmod +x ./phishingclub
Run the Interactive Installer
Launch the installer to begin the setup process:
/tmp/phishingclub --install
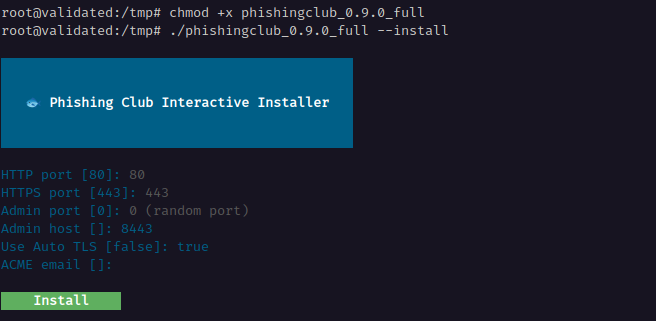
The CLI installer. The installer will prompt you to configure the following options:
Installation Configuration Options Configuration Description Default Value HTTP Port The HTTP port for the phishing server, used for special setups that revese proxy a with TLS termination. 80 HTTPS Port The HTTPS (TLS encrypted) port for the phishing server 443 Admin Port The HTTPS port for the administration Random port Admin Host The hostname for the administration server TLS certificate
(e.g., your server IP or domain name)localhost Auto TLS Enable TLS certificate management via Let's Encrypt
When disabled, creates a self-signed certificatefalse Complete Installation
After installation completes, the installer will display server details and login credentials.
Important: Copy these credentials as they are required to set up your administrative account.
Installation Output Information Item Description Generated Password Randomly generated password
Note: This password changes if the service restarts before setupPhishing HTTP Server URL for the HTTP phishing server endpoint Phishing HTTPS Server URL for the HTTPS phishing server endpoint Administration Server URL for the HTTPS administration page 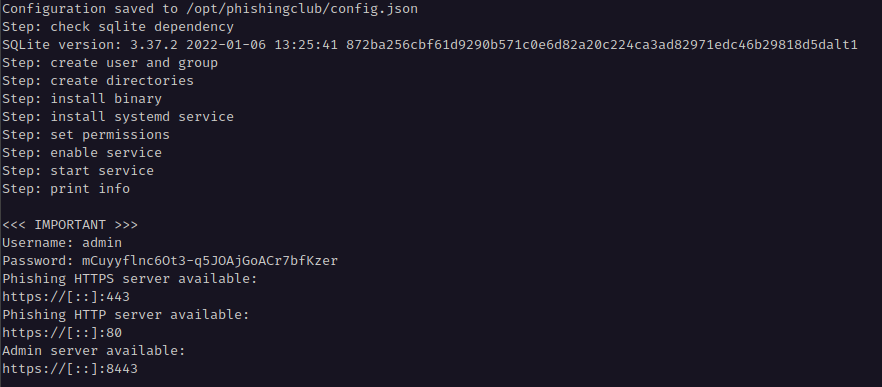
Output from an install with the credentials.
Setup
After installation, you must complete the setup process before Phishing Club is ready for use.
Note: If the application has been restarted after installation, you'll need to retrieve the temporary password from the system logs.
Access the administration page and log in using:
- Username:
admin - Password: The temporary password from installation output
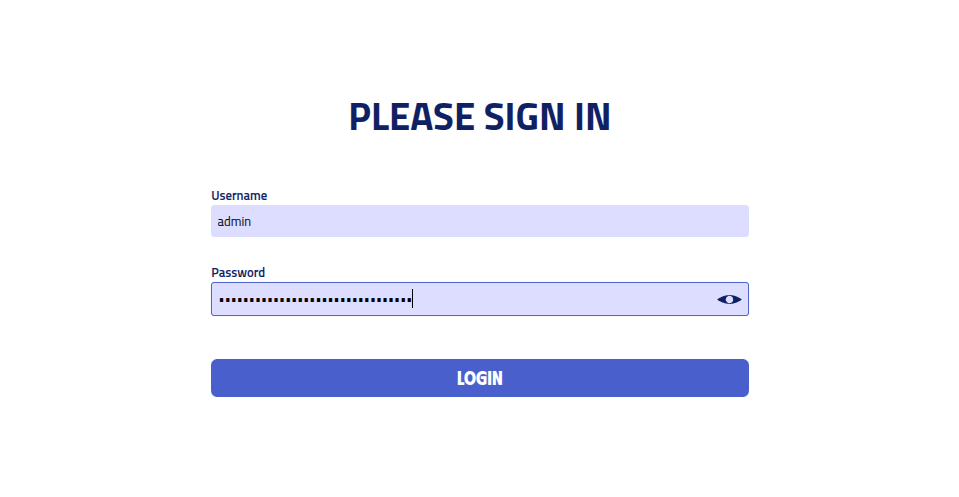
Setup Process
Configure Administrator Account
Set up your administrative account:
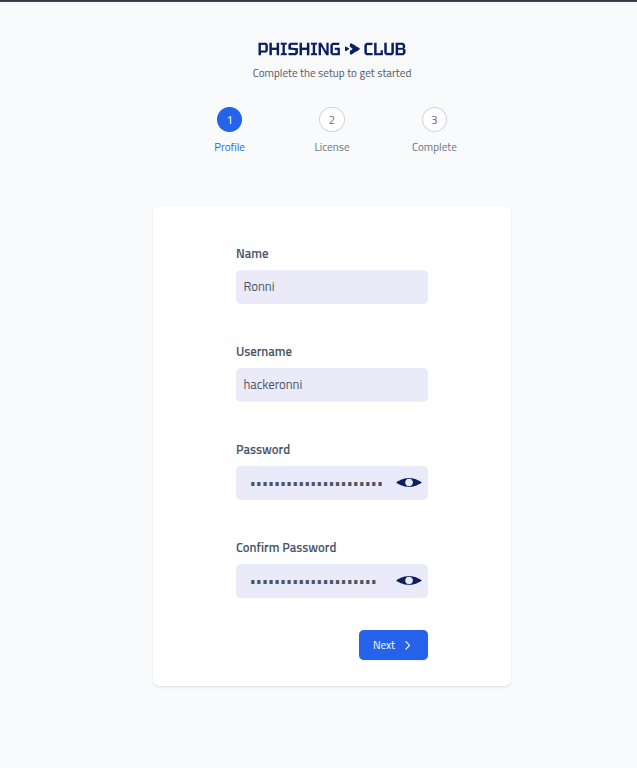
Setup Step 1: Profile Configuration Display Mode
Choose the
Display Mode, this will change how many menus/options are available, and can be changed later in settings.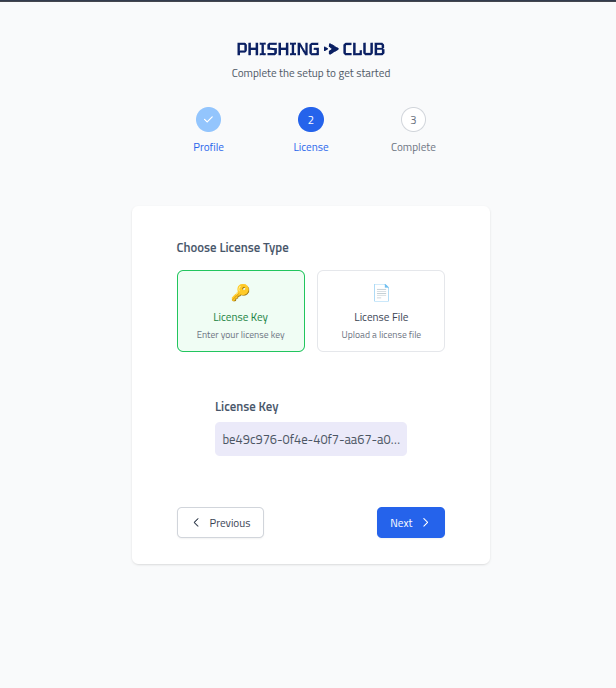
Setup Step 2: Display mode Templates
Choose if you want to install with example templates (emails and pages)
Setup Step 3: Optional templates Setup Completion
Setup Step 4: Complete setup
Complete! Phishing Club is now installed and ready for use. You can now begin creating your first phishing campaigns.
Automatic update
Phishing Club automatically checks for new versions and will notify you when updates are available.
When a new update is ready, an Update Available notification appears in the bottom
right corner of the page.
Click the Update button and follow the prompts to confirm the update process.
Manual Update
For manual updates, download the latest binary using the Update button in the page.
If your service was installed using the --install flag and runs via systemd, you
can perform the update using the --update flag on the new binary.
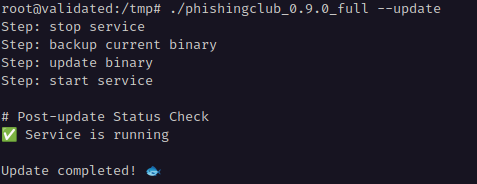
For manually configured instances, replace the current binary with the latest version and restart the service manually.
Uninstall
If you installed Phishing Club using the --install flag, you can uninstall using
the --uninstall flag.
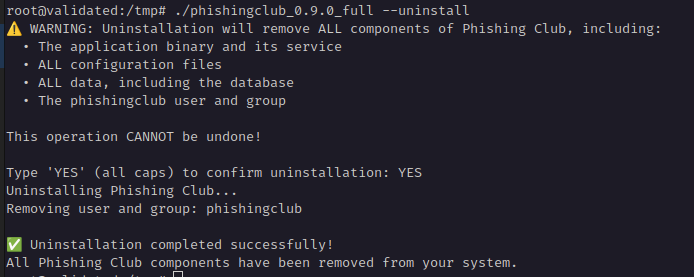
Warning: The uninstall process removes the user/group, systemd service, and all files including the database. This action cannot be undone.
./phishingclub --uninstall
You will be prompted to type YES in capital letters to confirm the uninstallation.
--uninstall flag.Configuration
The config.json configuration file, specified with the -config
flag, allows you to customize Phishing Club's behavior and operation.
Note: A service restart is required for configuration changes to take effect.
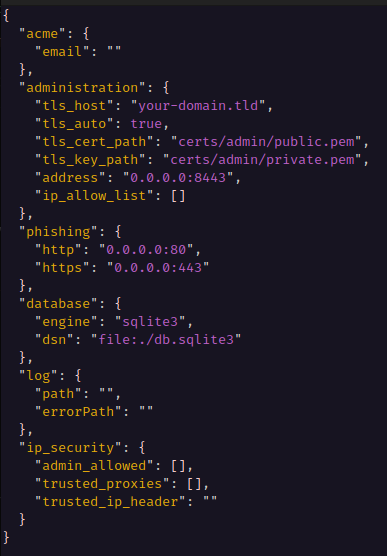
The configuration uses JSON format with the following properties:
| Configuration Key | Default Value | Description |
|---|---|---|
acme.email | Empty string | Email address for ACME certificate management ACME emails documentation |
administration.tls_host | localhost | Hostname for administration server TLS certificate (server IP address or domain name) |
administration.tls_cert_path | Empty string | File path to custom TLS certificate |
administration.tls_cert_key | Empty string | File path to custom TLS private key |
phishing.http | 80 | HTTP port for the phishing server |
phishing.https | 443 | HTTPS port for the phishing server |
database.engine | sqlite3 | Database engine type |
database.dsn | file:./db.sqlite3 | Database Data Source Name (connection string) |
config.path | Empty string | File path for stdout logging output |
config.errorPath | Empty string | File path for stderr logging output |
ip_security.admin_allowed | Empty array | Array of IP addresses allowed to access administration server Empty array allows all IPs |
ip_security.trust_proxies | Empty array | Array of trusted proxy IP addresses (or CIDRs) for forwarding client information Proxy configuration |
ip_security.trusted_ip_header | Empty string | HTTP header trusted for IP forwarding information. Thease are for the administration server. Not for the phishing server. |