Settings
Profile
The profile page handles username, password, MFA and API key management.
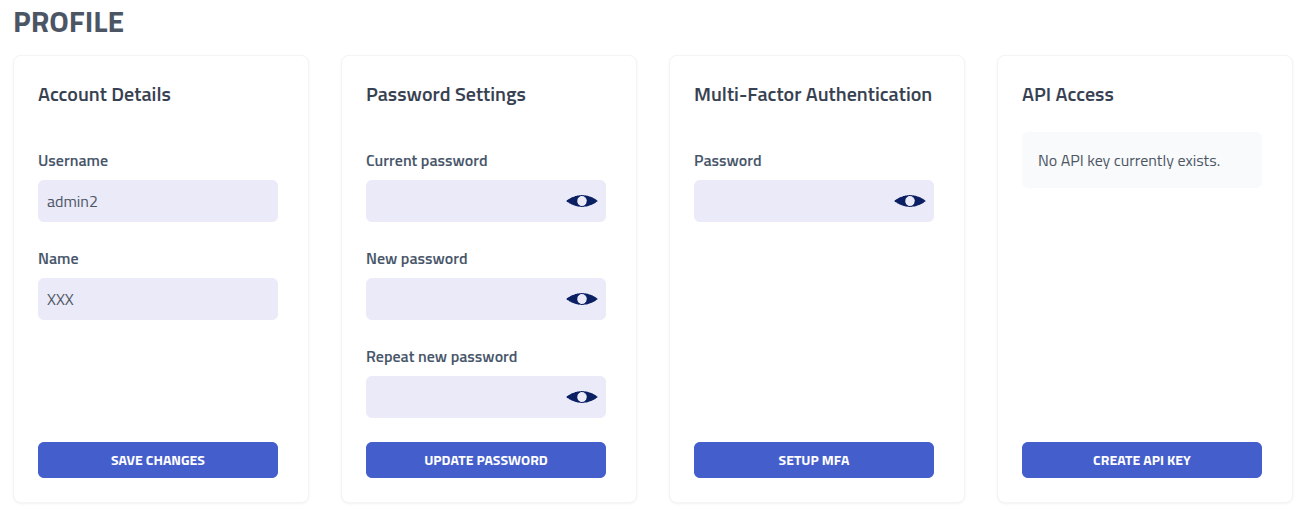
| Section | Description |
|---|---|
| Account Details | Modify username and display name |
| Password Security | Update account password - this invalidates active sessions |
| Multi-Factor Authentication | Enable TOTP authenticators. Recommended for all accounts |
| API Access Management | Configure API tokens for programmatic access |
Multi-Factor Authentication
Setup multi-factor for the account by clicking Setup MFA
If an account has MFA and is converted to a SSO user, then the MFA will be disabled.
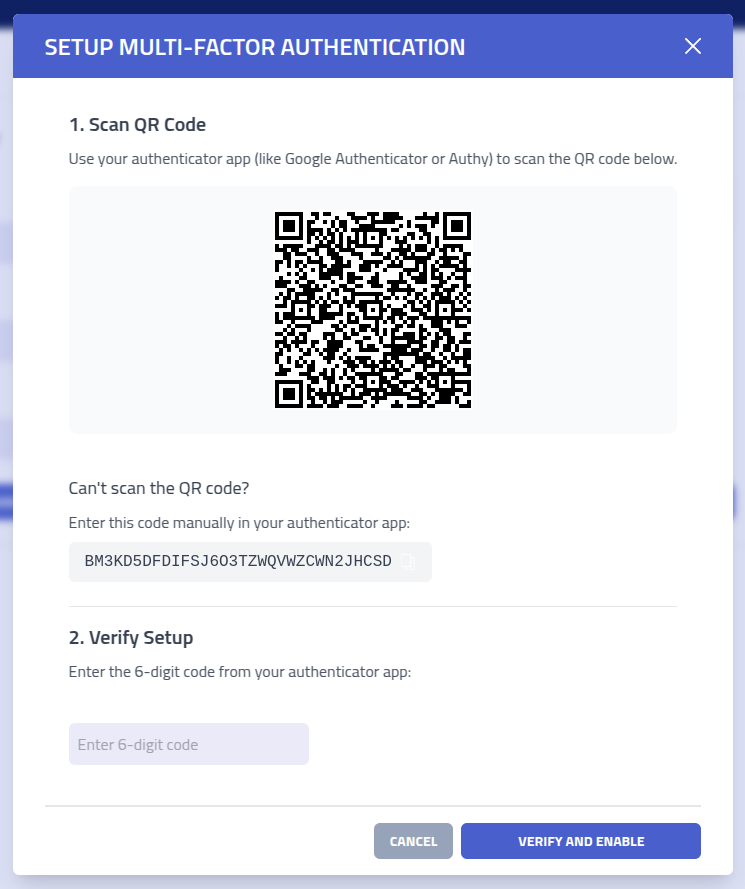
Complete the setup by scanning the QR code with your authenticator app (such as Google Authenticator, Authy, or Microsoft Authenticator) and then enter the generated verification code.
Important: After setup, you will receive backup recovery codes. Store these codes securely as they provide account access if your authenticator device becomes unavailable.
Should administrative access be lost, it can be recovered in the CLI by running -recover
API Key
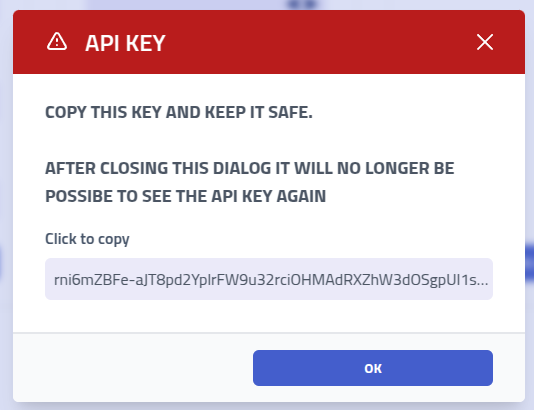
Accessing the API using the key can be done by adding a X-API header with the API
key as the value.
Note: The API is undocumented at the moment.
Sessions
Session management shows all active login sessions for your account. Each login creates a unique session that maintains your authentication state. This page enables monitoring of concurrent access, identification of unauthorized sessions, and session invalidation.
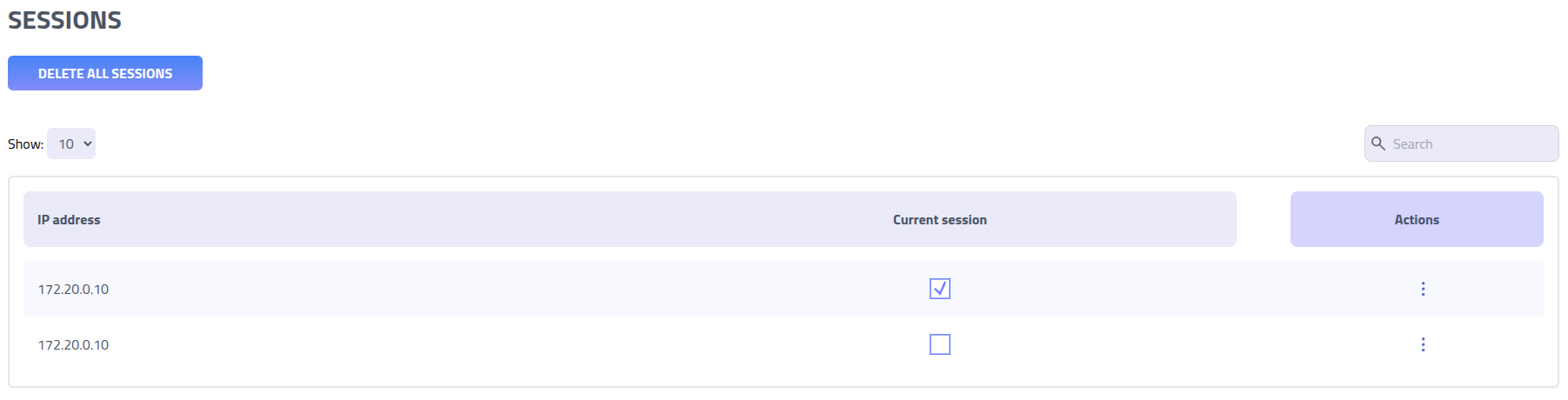
| Field | Description |
|---|---|
| IP Address | Source IP address associated with the session |
| Current Session Indicator | Indicator showing which session corresponds to your current browser session |
Users
Create, modify and delete administrative users. Use different accounts to help with audit logging and handling multiple API keys.
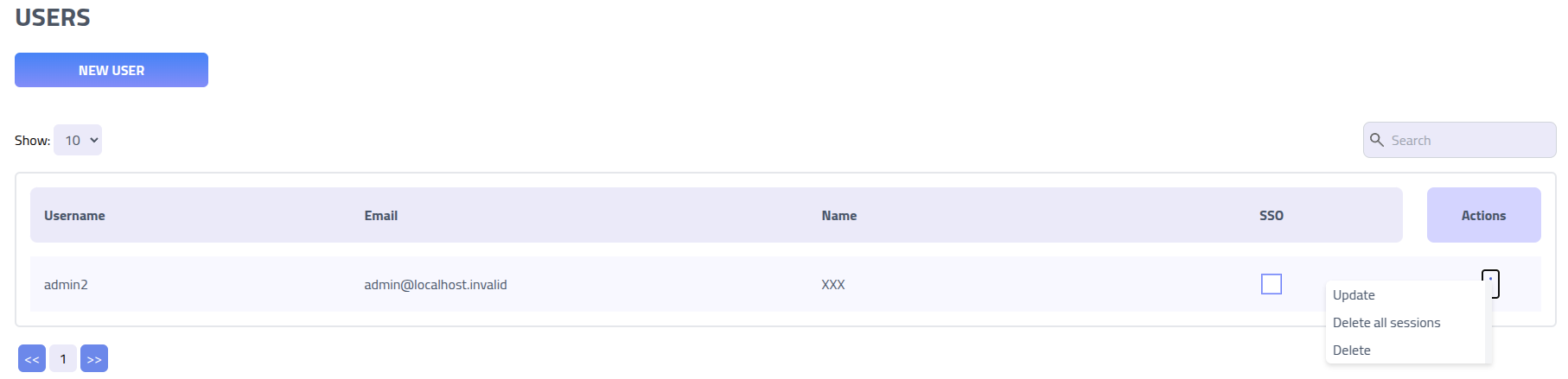
Force immediate logout for specific users by utilizing the Delete all sessions function,
which invalidates all active sessions.
Create user
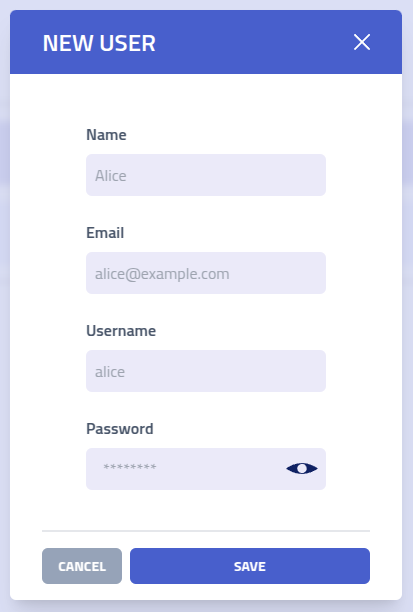
| Field | Description and Requirements |
|---|---|
| Display Name | Name for user identification in interfaces, reports, and audit logs |
| Email Address | Email address for user identification, notifications, and password recovery |
| Username | Login identifier for authentication. Should follow organizational naming conventions |
| Initial Password | Randomly generated password for initial account access. Users should change this upon first login |
Companies
Phishing Club supports handling multiple different companies within the same instance. This
means that all views such as the dashboard, emails and etc. are affected by if you are viewing
it in the Shared View or in a Company View.
Using this feature helps with analytics that match the company, and segregates company data so
it is less likely to that you send company 1 campaign to company 2. All resources that are
created in the Shared View
is available inside all Company Views. This makes it an ideal space to generic
campaign templates and etc. that can be reused for all companies or create a test recipient
group.

Data Export
Export organizational data for backup, compliance, or migration purposes. Use
Export Shared to download all global and shared resources that are available across
multiple organizations within your instance.
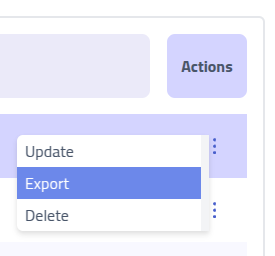
Access organization-specific data exports through the Actions menu for individual
companies, enabling data extraction while maintaining data isolation and privacy controls.
Create company
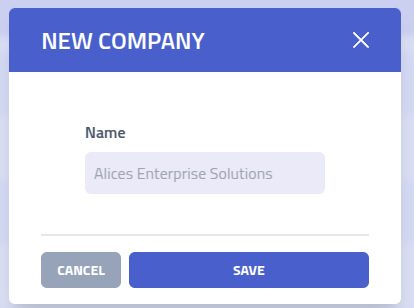
| Field | Description and Usage |
|---|---|
| Organization Name | Identifier for the client organization, used for data isolation, reporting, and administration within the multi-tenant environment |
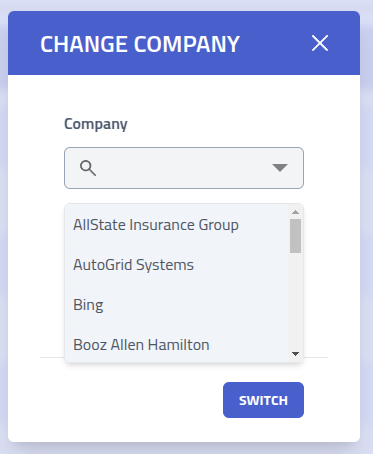
Switch company
Navigate between different companies is done by using the Change Company button in
the header.

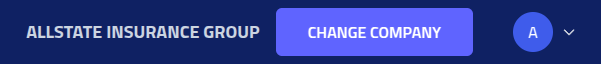
The currently active company context is displayed in the top navigation menu, showing which company data and campaigns you are currently managing:
Settings
The system settings provide control over platform-wide configuration.
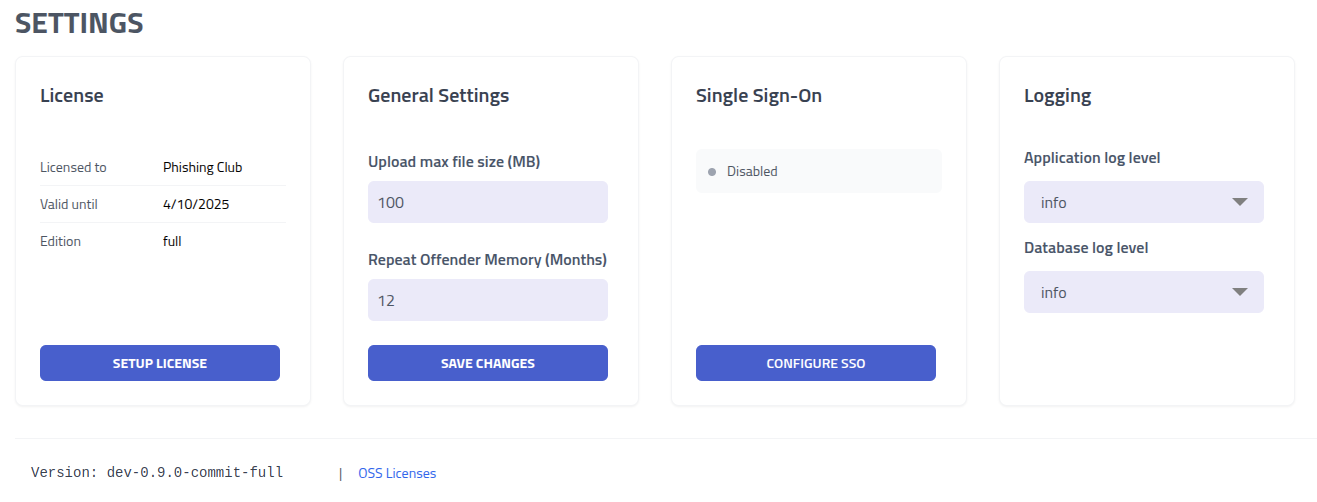
| Category | Configuration Options and Impact |
|---|---|
| Single Sign-On Integration | Configure SSO authentication with Microsoft 365 |
| General System Settings | Configure upload limits and repeat offender thresholds |
| System Logging | Adjust logging verbosity levels for troubleshooting, performance monitoring, and technical support |
| Data Import/Export | Manage data operations including imports. The import format is the export format of Templates project |
| Display Mode | Change if you want to use Phishing Club in Whitebox or
Blackbox
mode.Whitebox mode shows fewer menus and options. |
| Backup | Create an backup or download a backup. |
| Obfuscation template | Lets you change how Obfuscated landing pages are generated. The output is already
obfuscated when the option is enabled on a campaign, however this lets you wrap and customize
it. |
Import
The import system enables import of assets, landing pages, email templates, and other resources.
Download a example import file to understand the required structure: Phishing Club Import Example.zip
Import Process
Data import steps:- File Upload: Select and upload your structured .zip file using the import form interface
- Context Selection: Choose whether to import data into the current organization context or apply globally across all organizations
Required File Structure
Import files must follow a specific directory structure for processing and resource organization:
assets/- Global assets directory containing shared resources available across all templates and campaigns- Template Directories - Named folders containing
data.yamlconfiguration files with the following subdirectories:assets/- Template-specific multimedia resourcespages/- HTML landing page files for user interactionemails/- Email template content and designs
Template Configuration File
Each template directory requires a data.yaml configuration file that defines the template
structure, content relationships, and metadata for import processing:
name: "Professional Template Name"
pages:
- name: "Landing Page Name"
file: "pages/landing.html"
emails:
- name: "Email Template Name"
file: "emails/template.html"
envelope from: "[email protected]"
from: "Display Name <[email protected]>"
subject: "Compelling Email Subject Line" Import Processing and Validation
The import system validates and processes the following components:
- Global Assets: Shared resources from the root assets directory
- Template Assets: Component-specific multimedia and supporting files
- Landing Pages: HTML pages with embedded tracking capabilities
- Email Templates: Phishing simulation content and designs
Import Results Summary
Upon completion, the system provides an import summary detailing:
- Created Items: New resources successfully added to the platform
- Updated Items: Existing resources modified with new content or settings
- Skipped Items: Unchanged resources that already exist in the current state
- Error Reports: Information about any processing failures or validation issues
Single Sign-On
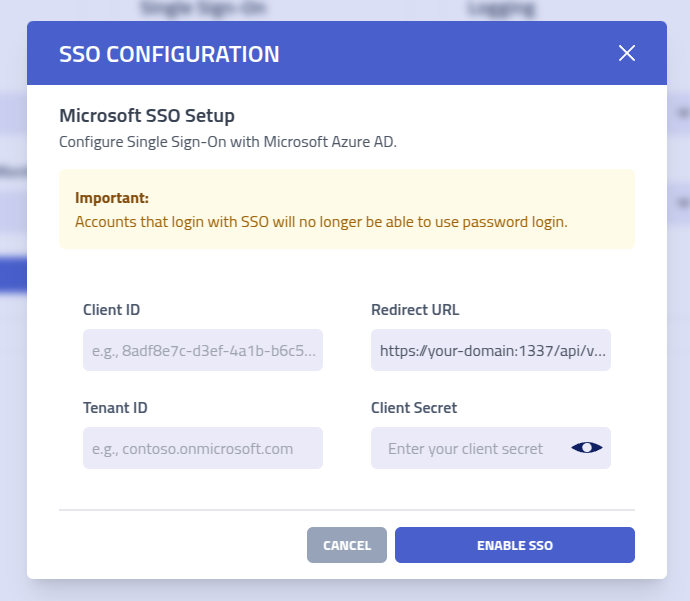
Configure Single Sign-On integration with Microsoft Azure Active Directory to streamline user authentication and leverage existing organizational identity management infrastructure.
SSO Migration Behavior
Important: SSO migration only occurs when a user chooses to log in via SSO. If a user continues to use password authentication, they will remain on password authentication. However, once a user logs in with SSO for the first time, their account is automatically migrated from password authentication to SSO-only authentication. This migration happens immediately and does not require the user to verify their current password.
What this means:
- Migration is user-initiated - Existing password users remain unchanged unless they click the SSO login button
- No password verification required - When a user clicks SSO login and authenticates via Azure AD with a matching email address, they immediately take over that account without needing to verify the existing password
- Password authentication is disabled - The user's password hash is permanently removed and they can only log in via SSO
- SSO is the authoritative authentication method - Azure AD becomes the single source of truth for user authentication
- No rollback - Once migrated, users cannot switch back to password authentication without manual intervention
Security Boundary
Critical: Because SSO migration does not verify passwords, SSO security is managed entirely at the Azure AD level, not within Phishing Club. To ensure only authorized users can access your instance, you must configure restrictions in Azure AD:
- In Azure Enterprise App settings, set "Assignment required" to
Yesunder Properties - Add specific users or groups under the "Users and groups" tab
- Configure conditional access policies and MFA requirements in Azure AD
Without these restrictions, any user in your Azure AD tenant could potentially authenticate via SSO. The security model assumes that Azure AD is the authoritative identity provider for your organization.
Azure Application Registration
Begin SSO configuration by registering a new application in your Microsoft Azure portal to establish the authentication relationship between Phishing Club and your organization's identity provider.
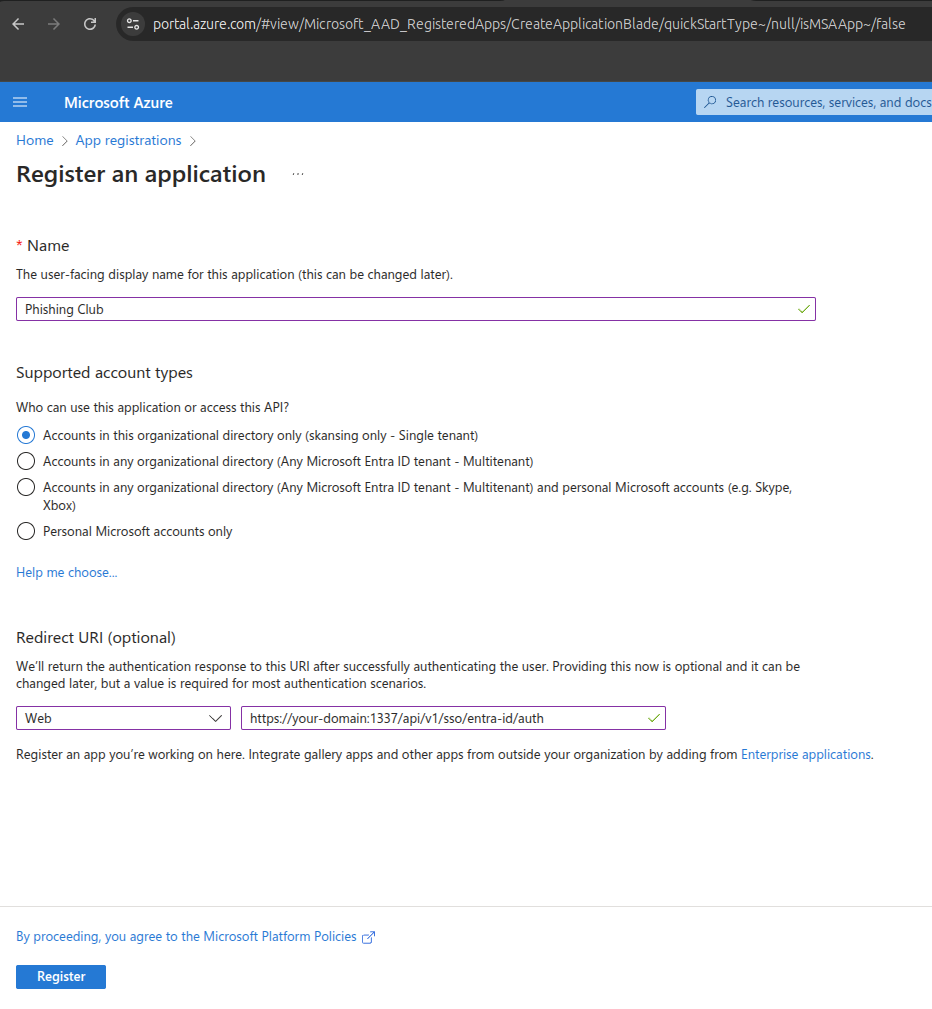
Configure the Redirect URI field with your Phishing Club instance URL:
your-domain.tld/api/v1/sso/entra-id/auth. This URL can be copied from the SSO
setup modal.
Extract the authentication identifiers from Azure and input them into Phishing Club:
- Copy the Application (client) ID and paste into the
Client IDfield - Copy the Directory (tenant) ID and paste into the
Tenant IDfield
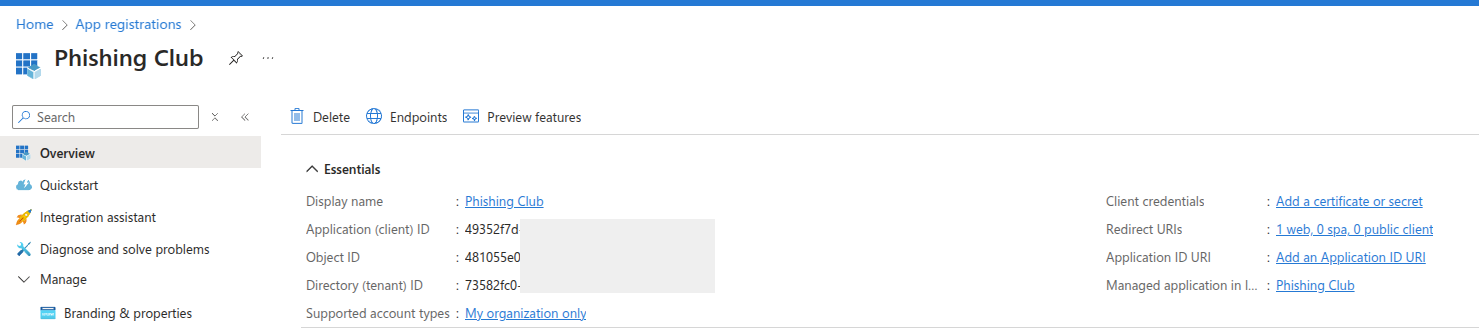
Create authentication credentials by clicking Add a certificate or secret
to generate the authentication token required for API communication between systems.
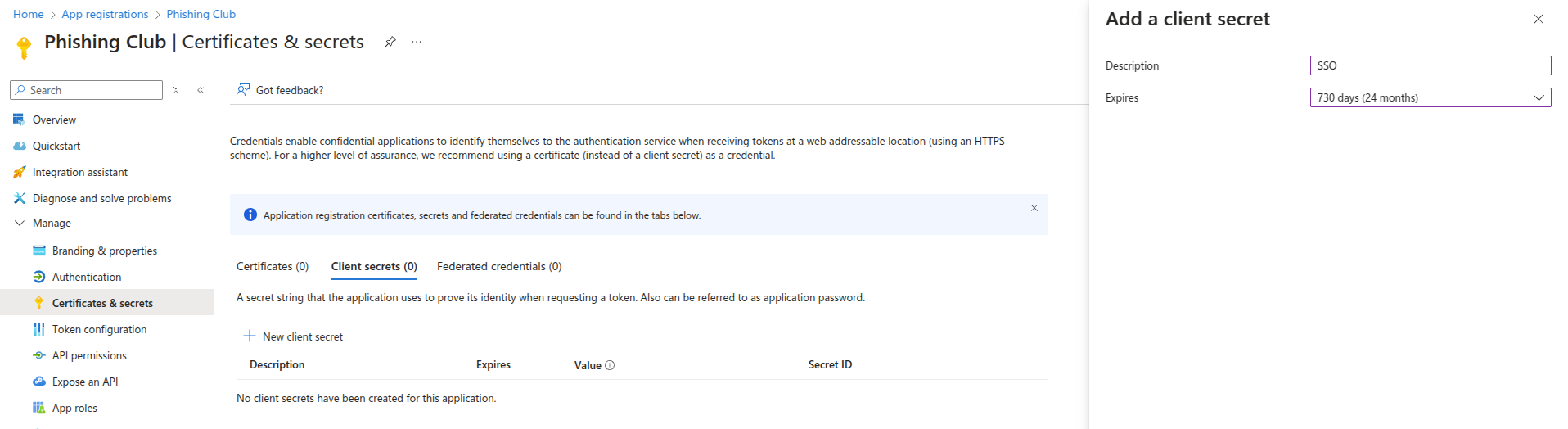
Generate a new client secret and copy the displayed Value into the
Secret field in Phishing Club. Important: This value is only displayed
once and cannot be retrieved later.

Complete the SSO configuration by clicking Enable SSO to activate authentication integration.
Users will now be able to authenticate using their organizational Microsoft 365 credentials to
access Phishing Club.

