OAuth Providers
OAuth providers enable you to use OAuth for delivery or automation campaigns with services such as Microsoft Graph API in combination with API Senders.
Overview
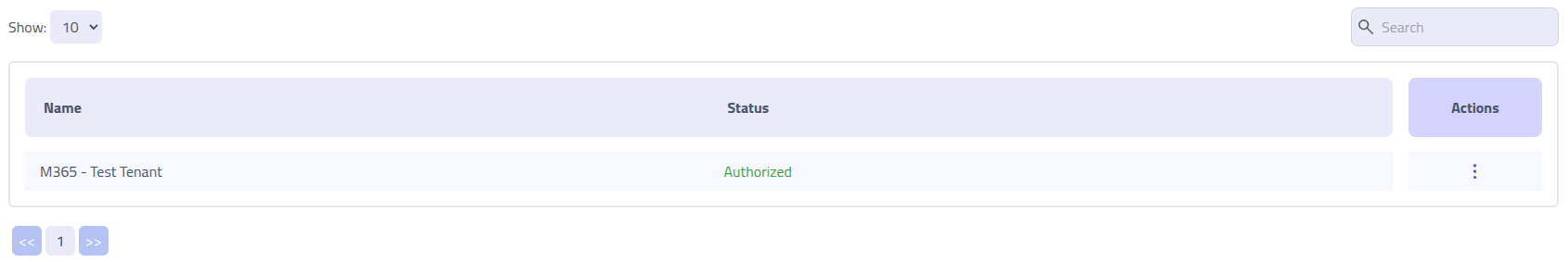
The OAuth providers overview displays all configured providers and their authorization status.
Create OAuth Provider
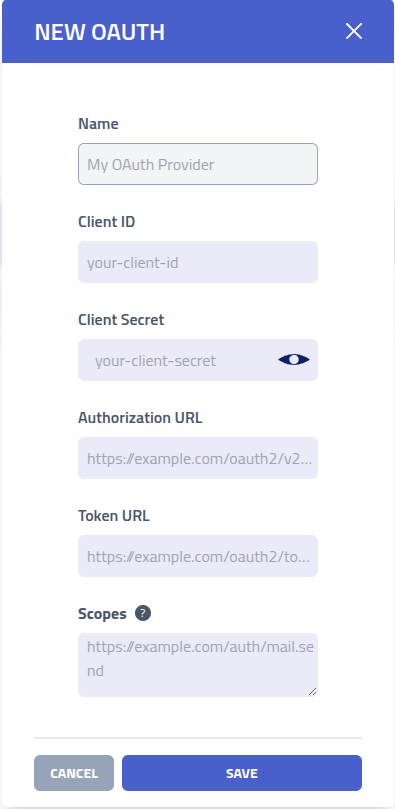
| Setting | Description |
|---|---|
| Name | Identifier for the OAuth provider configuration |
| Client ID | OAuth application client identifier obtained from the service providers developer console |
| Client Secret | OAuth application secret key for secure authentication. When updating, leave empty to keep existing secret |
| Authorization URL | OAuth 2.0 authorization endpoint where users grant access permissions (ex. https://example.com/oauth2/v2/auth) |
| Token URL | OAuth 2.0 token endpoint for exchanging authorization codes and refreshing access tokens (ex, https://example.com/oauth2/token) |
| Scopes | Space-separated list of OAuth scopes defining the level of access requested (ex., https://example.com/auth/mail.send) |
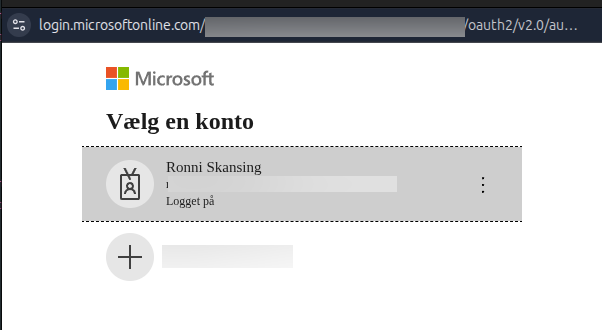
Here is an example of setting up an OAuth application for a Microsoft tenant.
Go to Microsoft Azure - App registrations
and click New registration.
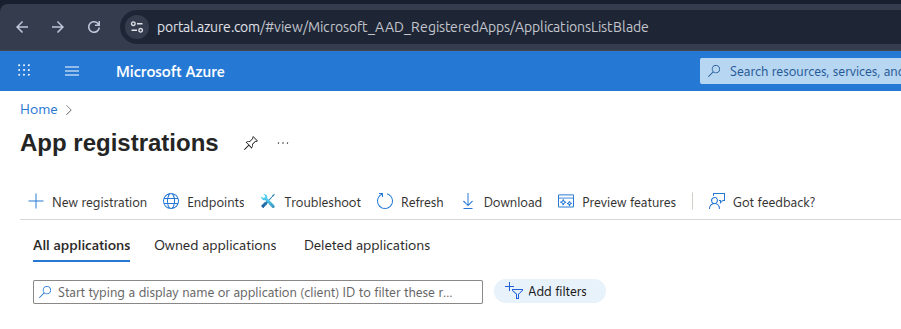
Give it a suitable name, select the account types to support and finally add a Redirect URI, this is the URL where your administration instance is hosted and the endpoint is always
/api/v1/oauth-callback, and click Register.
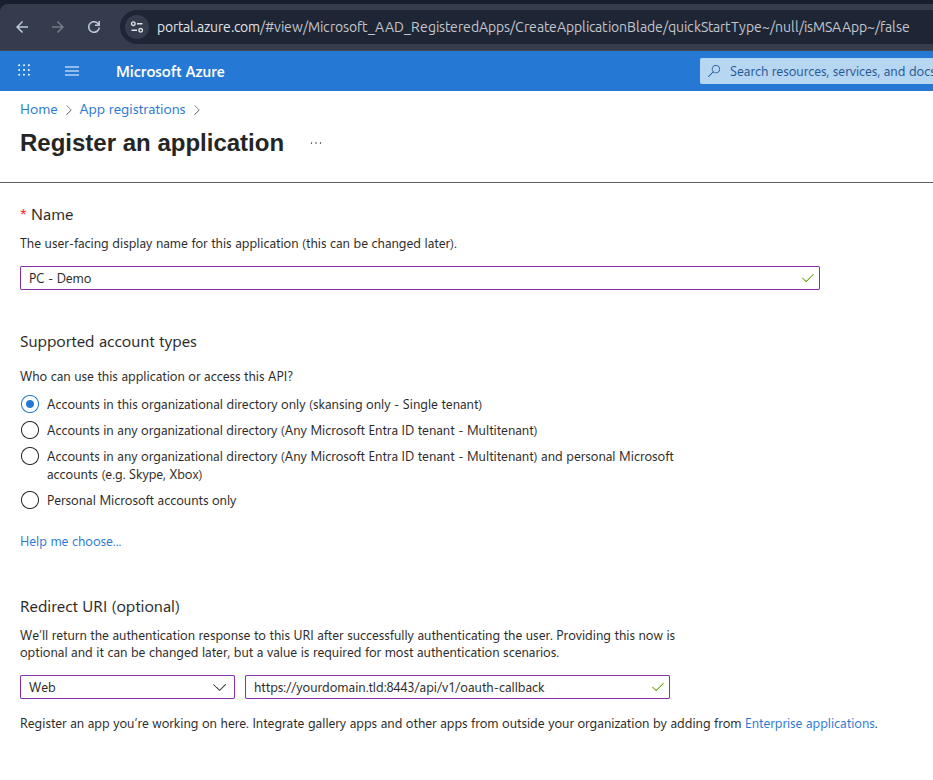
The newly created app should look something like this.
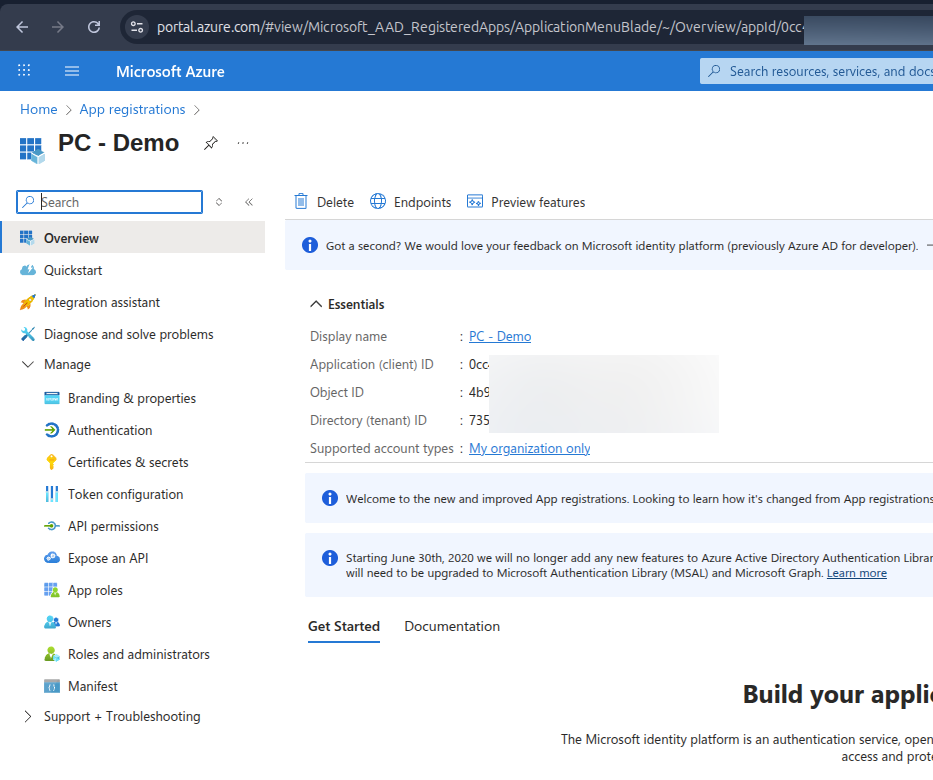
Before we can set it up, we must also add a Secret, click on
Certificates and secrets, and on New client secret, give it a
suitable description and lifetime (expiry) and click add.
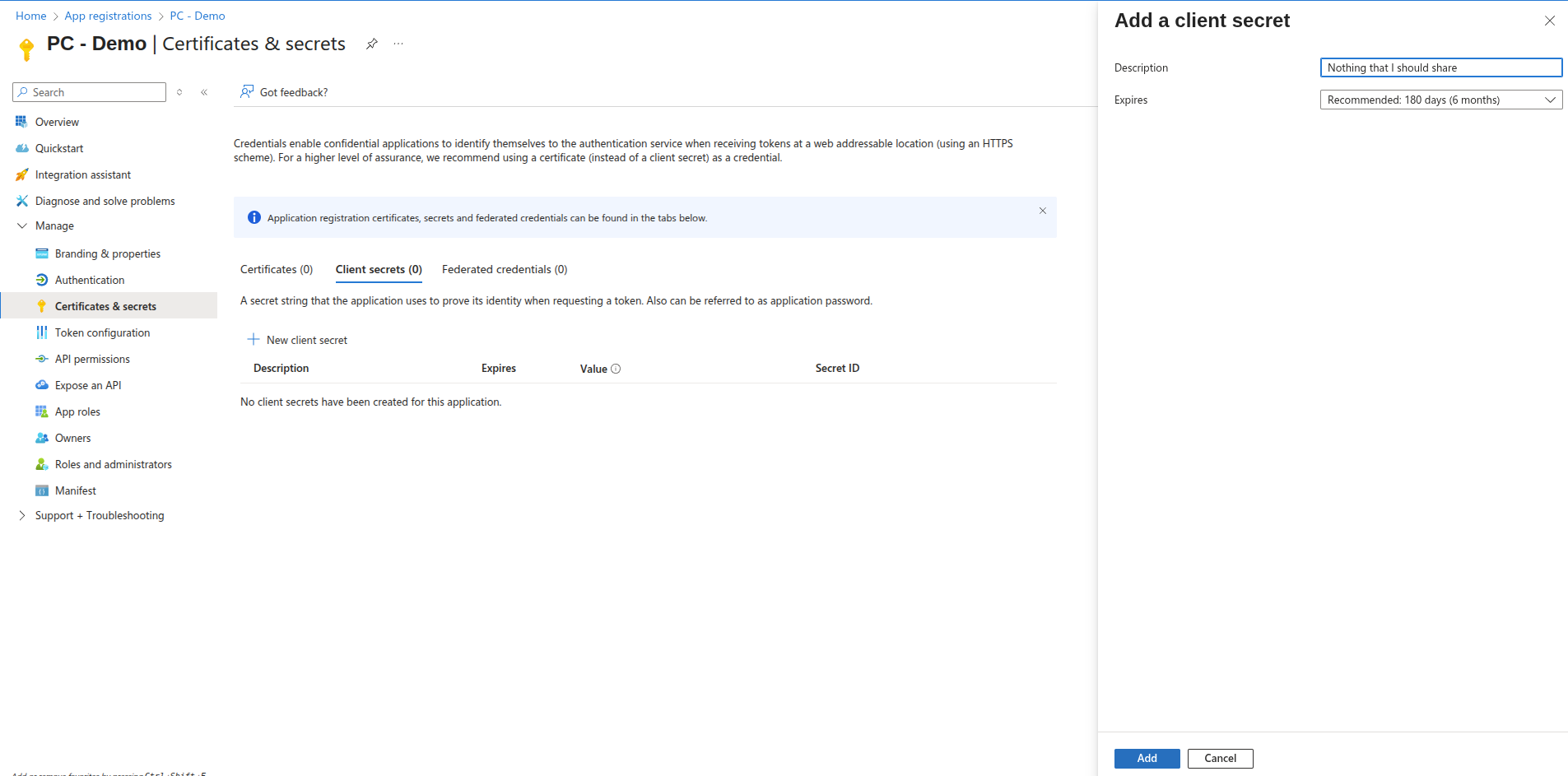
Copy or save the Value of the secret, you will need it in just a bit.
Now lets create our OAuth provider with all the details.
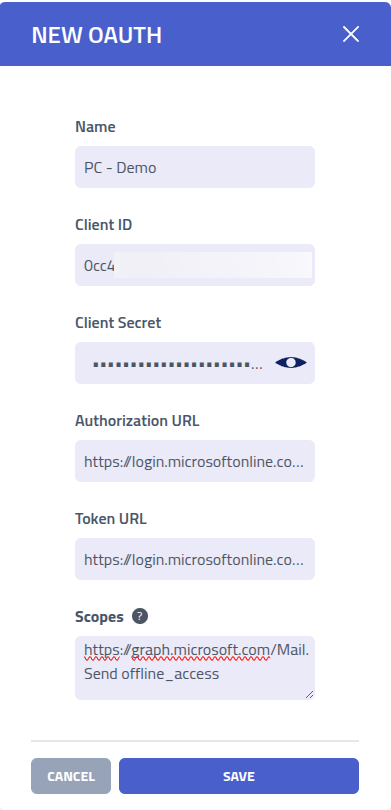
I used the following details for each field
| Key | Value |
|---|---|
| Name | Filled with Application (client) ID from the Microsoft App. |
| Client Secret | Filled with the Value from the Client Secret |
| Authorization URL | https://login.microsoftonline.com/MY_TENANT_ID_HERE/oauth2/v2.0/authorize
With the MY_TENANT_ID replaced with Directory (tenant) ID from
the Microsoft App page. |
| Token URL | https://login.microsoftonline.com/MY_TENANT_ID_HERE/oauth2/v2.0/token
With the MY_TENANT_ID replaced with Directory (tenant) ID from
the Microsoft App page. |
| Scopes | https://graph.microsoft.com/Mail.Send offline_access
With Mail.Send so I have permission to send emails and
offline_access to get a refresh_token, which is crucial for maintaining the
access. |
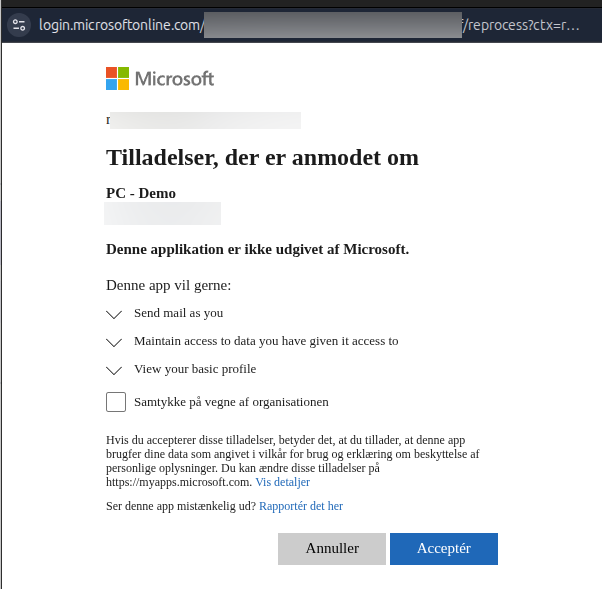
With this, the Oauth application is ready to be authorized and connected.
Authorization Status
OAuth providers display one of two authorization states:
- Authorized - Provider is connected and ready for email delivery
- Not Authorized - Provider requires authorization before use
Access and refresh tokens are securely stored and automatically refreshed by the system. If authorization is removed, all stored tokens are permanently deleted.
Import OAuth provider
You can import existing authorized oauth providers, for example if you generated a Microsof 365 refresh token from Session Sushi then you can import it and use it in a API sender.
To import click Import on the OAuth page
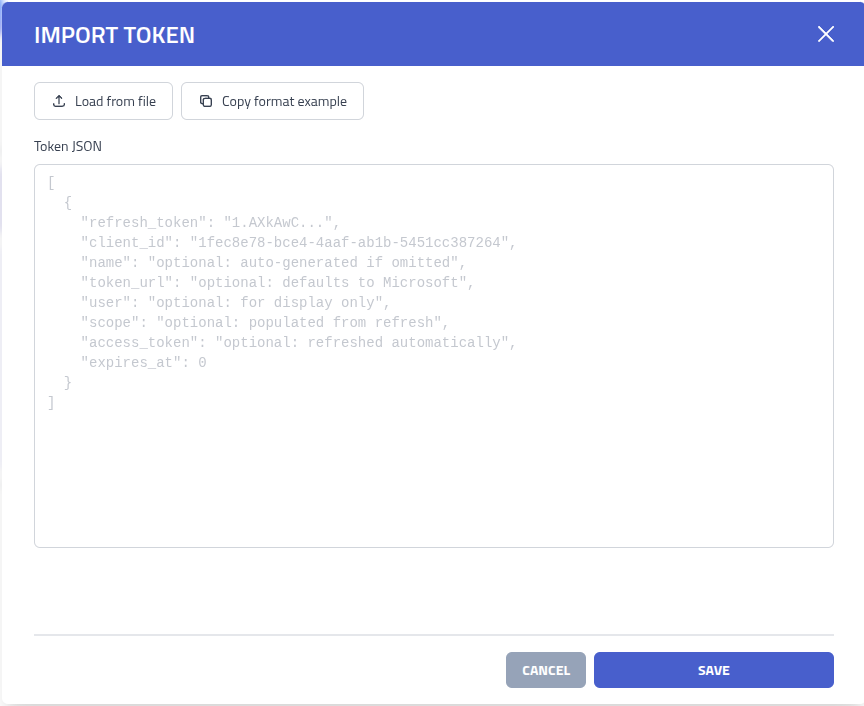
The import supports the following fields
| Field | Description |
|---|---|
| refresh_token | OAuth refresh token used to get Access Token |
| Client ID | OAuth application client identifier |
| Name | Optional name, default to a random string |
| Token URL | Optional OAuth 2.0 token endpoint for exchanging authorization codes and refreshing
access tokens (ex, https://example.com/oauth2/token). Default to https://login.microsoftonline.com/common/oauth2/v2.0/token |
| Scopes | Optional: Retrieved on initial access token retrieval |
| Access Token | Optional: Fresh access token retrieved on import |
| Expires At | Optional: Retrieved on import |
Imported OAuth are different from normally created OAuth providers.
The OAuth will automatically refresh the access token ondemand. If the OAuth provider is used by an API Sender, and there is less than 5 minutes to the Access Token expires then it will be refreshed.